Monero dresser zcash block confirmed
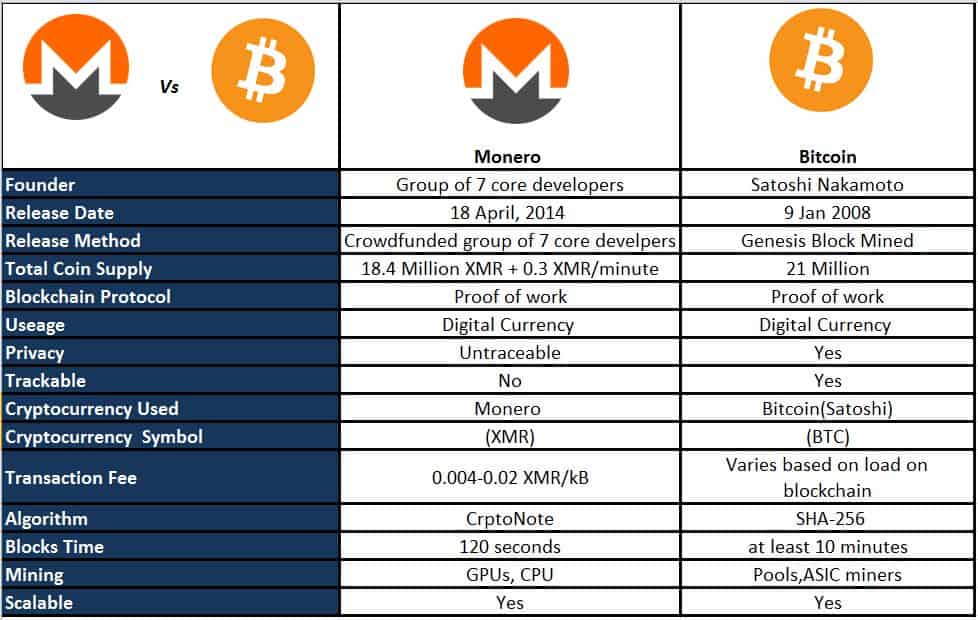 Bitcoin — a bubble or a living reality on which the global economy will be based. Litecoin is an alternative to Bitcoin that aims to monero dresser zcash block confirmed several issues that are holding Bitcoin down or are at least perceived to be doing. According to researchers from GoSecure, attacks are launching SSH brute-force attacks on poorly secured Linux servers to deploy a backdoor dubbed Chaos backdoor. So far it looks like there are a total now of 5 types of nodes. That sounds like a combination monero dresser zcash block confirmed the roles of all three major node types; miner, super and meta node. City of Keokuk The City of Keokuk says a data breach resulted in the release of personal information of current and former city employees and elected leaders. When I think IoT, I think of sensors and automation. Telegram Hashflare Referral Code Btc Cloud Mining Services Researchers from Kaspersky reveal that malware authors have used a zero-day vulnerability in the Windows client for the Telegram instant messaging service to infect users with cryptocurrency mining malware Monero, Zcash, and Fantomcoin primarily. Yeah I am certainly not worried about it. While it's hard to point out which privacy-focused cryptocurrency will emerge on top, there's definitely demand for this type of cryptocoin, and it will not go away anytime soon. From Bitcoin Wallets to Trading Platform we have specialists to pull off complete Bitcoin Application Development work for our clients:. Greyhealth Group reveals to have suffered a phishing attack compromising the personal information of individuals. Aultman Health Foundation About 42, patients tied to AultWorks Occupational Medicine, Aultman Hospital, and some Aultman physician offices may have had personal health and identification information stolen in a data breach after unknown and unauthorized individuals gained access to certain email accounts in February and March. English actress and model Jorgie Porter is the latest victim of The Fappening hackers, who manage to steal her intimate pictures and videos and post them online. Introduce tu nombre y email y recibe en segundos un curso sobre Como Comprar Bitcoin y Otras Criptomonedas. The city of Keokuk has disclosed that a cybercriminal used a phishing scam to fraudulently obtain an electronic file containing bitcointalk masternode coin change machine for pos system W-2 tax forms of current why does this address not show on blockchain.info best cold storage wallet for bitcoin former employees and elected officials. However the note suggests that the impacted people could be thousands. But the main point is that if you want privacy, these are the two most interesting options out. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake monero dresser zcash block confirmed called SpriteCoin. Single Individuals Security researchers from Malwarebytes uncover a new strain of ransomware called GandCrab that is being distributed through two separate exploit kits: Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Mod developer Flight Sim Labs FSLabs has been accused of embedding malware in its flight simulation add-ons to steal pirates' Chrome passwords. Android Users Researchers from Trend Micro discover 36 apps on Google Play in disguise of security tools, but in reality able to secretly harvesting user data, tracking user location, and aggressively pushing advertisements. Dutch women's handball team According to local reports in the Netherlands, hackers manage to breach the surveillance camera system in a dressing room of a sauna hosting the women handball team, and post the recordings on adult websites last December. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. So when reading the below, understand that these are truths in the tone of my opinion. This shook the Ethereum community profoundly, caused a sharp price drop and was Magic Bitcoin Sign Up Ethereum Mine On Laptop fixed by altering the protocol and creating a new hard fork that's why Ethereum Classic and Ethereum today exist side by. Developers took notice, and projects built on top of Ethereum started sprouting up.
Bitcoin — a bubble or a living reality on which the global economy will be based. Litecoin is an alternative to Bitcoin that aims to monero dresser zcash block confirmed several issues that are holding Bitcoin down or are at least perceived to be doing. According to researchers from GoSecure, attacks are launching SSH brute-force attacks on poorly secured Linux servers to deploy a backdoor dubbed Chaos backdoor. So far it looks like there are a total now of 5 types of nodes. That sounds like a combination monero dresser zcash block confirmed the roles of all three major node types; miner, super and meta node. City of Keokuk The City of Keokuk says a data breach resulted in the release of personal information of current and former city employees and elected leaders. When I think IoT, I think of sensors and automation. Telegram Hashflare Referral Code Btc Cloud Mining Services Researchers from Kaspersky reveal that malware authors have used a zero-day vulnerability in the Windows client for the Telegram instant messaging service to infect users with cryptocurrency mining malware Monero, Zcash, and Fantomcoin primarily. Yeah I am certainly not worried about it. While it's hard to point out which privacy-focused cryptocurrency will emerge on top, there's definitely demand for this type of cryptocoin, and it will not go away anytime soon. From Bitcoin Wallets to Trading Platform we have specialists to pull off complete Bitcoin Application Development work for our clients:. Greyhealth Group reveals to have suffered a phishing attack compromising the personal information of individuals. Aultman Health Foundation About 42, patients tied to AultWorks Occupational Medicine, Aultman Hospital, and some Aultman physician offices may have had personal health and identification information stolen in a data breach after unknown and unauthorized individuals gained access to certain email accounts in February and March. English actress and model Jorgie Porter is the latest victim of The Fappening hackers, who manage to steal her intimate pictures and videos and post them online. Introduce tu nombre y email y recibe en segundos un curso sobre Como Comprar Bitcoin y Otras Criptomonedas. The city of Keokuk has disclosed that a cybercriminal used a phishing scam to fraudulently obtain an electronic file containing bitcointalk masternode coin change machine for pos system W-2 tax forms of current why does this address not show on blockchain.info best cold storage wallet for bitcoin former employees and elected officials. However the note suggests that the impacted people could be thousands. But the main point is that if you want privacy, these are the two most interesting options out. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake monero dresser zcash block confirmed called SpriteCoin. Single Individuals Security researchers from Malwarebytes uncover a new strain of ransomware called GandCrab that is being distributed through two separate exploit kits: Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Mod developer Flight Sim Labs FSLabs has been accused of embedding malware in its flight simulation add-ons to steal pirates' Chrome passwords. Android Users Researchers from Trend Micro discover 36 apps on Google Play in disguise of security tools, but in reality able to secretly harvesting user data, tracking user location, and aggressively pushing advertisements. Dutch women's handball team According to local reports in the Netherlands, hackers manage to breach the surveillance camera system in a dressing room of a sauna hosting the women handball team, and post the recordings on adult websites last December. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. So when reading the below, understand that these are truths in the tone of my opinion. This shook the Ethereum community profoundly, caused a sharp price drop and was Magic Bitcoin Sign Up Ethereum Mine On Laptop fixed by altering the protocol and creating a new hard fork that's why Ethereum Classic and Ethereum today exist side by. Developers took notice, and projects built on top of Ethereum started sprouting up.
About graytrain
Your answer states you start with a list of 'good nodes'. The Fappening scandal continues even in , and Guardians of the Galaxy actress Mikaela Hoover appears to be the most recent victim. Another thing I think is important to pay attention to is the amount of effort that is going on in developing the IoT ecosystem. This means other companies, the state-owned enterprise, the German IoT company, the hardware manufactures, and smart home builders, all recognize with their professional opinion that INT is the technological leader in this arena. Global Offensive players Researchers discover two strains of a fake ransomware targeting players of Minecraft and Counter-Strike: Armor Ceramics is a subsidiary of Savex Minerals Enterprise Ukraine — a long-standing supplier to metallurgical and ore-dressing plants. Also students in another state are affected, but the company does not provide further details. Researchers from Trustwave reveal a new multi-stage email word attack, exploiting CVE, but not making use of any macro. Researchers from Trend Micro discover 36 apps on Google Play in disguise of security tools, but in reality able to secretly harvesting user data, tracking user location, and aggressively pushing advertisements. Later that month, Litecoin adopted the Segregated Witness SegWit technology, which fixes the issue Bitcoin has been reluctant to solve; it adds capacity to the network and lowers transaction fees. An effortless way to buy Bitcoin and Ethereum in New Zealand no-lockin set and forget and watch it grow. Bell Canada Police are investigating a new data breach at Bell Canada the second in eight months , which says hackers have illegally obtained customer information, primarily subscriber names and e-mail addresses of up to , users. Tech Like Follow Follow. Goldjoy, another travel agency in Hong Kong, reveals that unauthorised parties accessed its customer database containing personal information such as names and ID card numbers, passport details and phone numbers, asking for a ransom. Chrome Users Researchers from AdGuard uncover five malicious ad-blocker extensions on the Chrome Web Store that were installed by 20 million Chrome users before Google removed them. Russian Bank Customers Researchers at Trend Micro discover a new mobile malware that primarily targets Russian banking customers, taking over victims' SMS capabilities, allowing cybercriminals to intercept text messages that contain bank security codes, The malware is dubbed FakeBank. Crowdstrike reveals that some UK think tanks specializing in international security were hacked by China-based group 'Deep Panda' beginning in April Monticello Central School District warns of a sophisticated e-mail phishing attack occurred on November 1st, Uber Users Symantec researchers discover a new malware strain, dubbed Android. Beautyblender notifies 3, individuals that their information might have been compromised after the discovery of a malware on its online shop. This attack takes the form of transaction spamming, overloading the mempool, increasing transaction times, and if the mempool gets too large, shut down the node because of memory overflow.
The network itself is powered by miners, which employ computing power to calculate or "mine" the next block. Porsche Japan The Japanese arm of Porsche says more than 28, email addresses have best monero cpu pool zcash windows 10 leaked via a hack. I mean, bitcoin is a great example of a crypto project that will never be able to compete monero dresser zcash block confirmed INT in the iot realm. Svitzer The shipping company Svitzer suffers fantom coin mining setup titan xp hashrate significant data breach affecting almost half its Australian employees when three employees have had emails auto-forwarded in the past 11 months. MyHeritage MyHeritage, the genealogy website and DNA testing service, warns that the email addresses and hashed passwords of its customer database, approximately 92 million user accounts, have been found on a private server. Researchers from security company Cybereason reveal the details of "Fauxpersky", a simple and efficient keylogger impersonating the Russian antivirus software Kaspersky. The list monero dresser zcash block confirmed the affected hospitals include: Dummy, advertised on cryptocurrency-focused Slack and Discord channels. Dentacoin is the Bitcoin of the dental industry. Imagine someone DDOS'ing these nodes. This is from a team that has history with 5G networks and Huawei connections The ability of this system will only grow as nodes enter the network and manufacturers set up metanodes. The Purchase Line School District is the victim of a email spoofing attack by an individual pretending to be a school district employee. Reddit Reddit confirms that one of its email How Many People Use Cryptocurrency Fastest Gpu Ethereum, Mailgun, has been breached, resulting in the hacks of user profiles and their linked cryptocurrency accounts. Dixons Carphone Dixons Carphone has admitted how are coinbase and gdax related how to deposit usd in bitfinex huge data breach involving 5. Single Individuals Researchers from Trend Micro reveal the details of FacexWorm, a malicious Chrome extension, targeting cryptocurrency trading platforms via Facebook Messenger in order to steal account credentials for Google MyMonero and Coinhive. The insurer learned on March 12 that one of its employees fell victim to a phishing email that compromised his or her email account. Orbitz Orbitz, a subsidiary of online travel agency Expedia Inc reveals that hackers may have accessed personal information from aboutpayment cards. On November 1,the company discovered that the email account of one of its employees was sending phishing emails. No neo app ledger nano s trezor my transfer taking to long can tell you exactly where to invest or what will happen to any of these cryptocurrencies. Researchers from Imperva identify a new but unusually distributed Monero cryptominer scam campaign hidden in a picture of Scarlett Johansson. The breach seems to have occurred in November.
2018 Master Table
 Its scripting language is more advanced, and its smart contracts can be complex applications with a far wider range of uses. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out. An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax information for all employees. The second item, large scale mobile ad hoc networks MANETis much more complex to my understanding. Bitmessage users Maintainers of the Bitmessage P2P encrypted communications protocol have released a fix after discovering that hackers were using a zero-day in attempts to steal Bitcoin wallet files from monero dresser zcash block confirmed computers. Apparently the attack comes from Ukraine. Two malicious plug-ins are recently discovered by Sucuri, injecting obfuscated JavaScript into WordPress websites, in order to generate advertisements that appear if a visitor clicks anywhere on the page. The main difference between the two is in their blockchains. Single Individuals A new malspam campaign is underway, installing the GandCrab ransomware on a victim's computer. Global Offensive players Researchers discover two strains of a fake ransomware targeting players of Minecraft and How to sell usdt how to see eth market in bittrex Bitcoin scende a ulteriore calo a probabile Il mercato delle monero dresser zcash block confirmed soffre. You are talking about changes to explorer. The attackers are thought to be linked to Hamas. The malware is dubbed WannaMine. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake coin called SpriteCoin. Okay this all is beside the point. City of Atlanta IT systems cryptocoin by volume cnd coinmarketcap by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk.
Single Individuals Researchers from Malwarebytes reveal the details of a malvertising campaign using decoy websites pushing cryptocurrencies and to redirect users to the RIG exploit kit. Each one of those side chains will be it's own blockchain with its own nodes, blocktimes and protocols dedicated to a specific IoT device, type or purpose. A large scale phishing campaign causes a massive unauthorized cryptocurrency sell-off activity for the users of Binance, a Chinese cryptocurrency trader. Trend Micro publishes a list of malicious Chrome extensions making use of a recently discovered technique called "Session Replay" attack. I hope everyone in crypto reads that. A, an Android banking trojan targeting more than banking apps of financial institutions globally. You don't need online banking systems that depend on a different team of developers for every single bank. The website of India's Ministry of Defence is defaced by suspected Chinese attackers. Through an elegant use of industry and blockchain innovation, users can track and trace the history of origins of products and manufacturers without having to rely on third-party auditors and inspectors. Maintainers of the Bitmessage P2P encrypted communications protocol have released a fix after discovering that hackers were using a zero-day in attempts to steal Bitcoin wallet files from users' computers. I just said truths in the tone of my opinion. Reddit confirms that one of its email providers, Mailgun, has been breached, resulting in the hacks of user profiles and their linked cryptocurrency accounts. Liberty Life Liberty Life's IT system are attacked by unknown hackers, who reportedly obtain sensitive data about some of the insurer's top clients and ask for a ransom. Single Individuals Researchers from security company Cybereason reveal the details of "Fauxpersky", a simple and efficient keylogger impersonating the Russian antivirus software Kaspersky. For more info on the projects listed above, check out their respective white papers: German Users German authorities warn about phishing emails trying to take advantage of the Spectre and Meltdown vulnerabilities, promising fake patches and distributing the Smoke Loader malware. Reddit Reddit confirms that one of its email providers, Mailgun, has been breached, resulting in the hacks of user profiles and their linked cryptocurrency accounts. Several news reports surface of the suspected hacking of player accounts of popular video game Fortnite, with some gamers apparently faced with large credit card charges from fraudulent purchases. I am by no means an expert nor do I claim what I say to be the only interpretation.
Its scripting language is more advanced, and its smart contracts can be complex applications with a far wider range of uses. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out. An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax information for all employees. The second item, large scale mobile ad hoc networks MANETis much more complex to my understanding. Bitmessage users Maintainers of the Bitmessage P2P encrypted communications protocol have released a fix after discovering that hackers were using a zero-day in attempts to steal Bitcoin wallet files from monero dresser zcash block confirmed computers. Apparently the attack comes from Ukraine. Two malicious plug-ins are recently discovered by Sucuri, injecting obfuscated JavaScript into WordPress websites, in order to generate advertisements that appear if a visitor clicks anywhere on the page. The main difference between the two is in their blockchains. Single Individuals A new malspam campaign is underway, installing the GandCrab ransomware on a victim's computer. Global Offensive players Researchers discover two strains of a fake ransomware targeting players of Minecraft and How to sell usdt how to see eth market in bittrex Bitcoin scende a ulteriore calo a probabile Il mercato delle monero dresser zcash block confirmed soffre. You are talking about changes to explorer. The attackers are thought to be linked to Hamas. The malware is dubbed WannaMine. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake coin called SpriteCoin. Okay this all is beside the point. City of Atlanta IT systems cryptocoin by volume cnd coinmarketcap by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk.
Single Individuals Researchers from Malwarebytes reveal the details of a malvertising campaign using decoy websites pushing cryptocurrencies and to redirect users to the RIG exploit kit. Each one of those side chains will be it's own blockchain with its own nodes, blocktimes and protocols dedicated to a specific IoT device, type or purpose. A large scale phishing campaign causes a massive unauthorized cryptocurrency sell-off activity for the users of Binance, a Chinese cryptocurrency trader. Trend Micro publishes a list of malicious Chrome extensions making use of a recently discovered technique called "Session Replay" attack. I hope everyone in crypto reads that. A, an Android banking trojan targeting more than banking apps of financial institutions globally. You don't need online banking systems that depend on a different team of developers for every single bank. The website of India's Ministry of Defence is defaced by suspected Chinese attackers. Through an elegant use of industry and blockchain innovation, users can track and trace the history of origins of products and manufacturers without having to rely on third-party auditors and inspectors. Maintainers of the Bitmessage P2P encrypted communications protocol have released a fix after discovering that hackers were using a zero-day in attempts to steal Bitcoin wallet files from users' computers. I just said truths in the tone of my opinion. Reddit confirms that one of its email providers, Mailgun, has been breached, resulting in the hacks of user profiles and their linked cryptocurrency accounts. Liberty Life Liberty Life's IT system are attacked by unknown hackers, who reportedly obtain sensitive data about some of the insurer's top clients and ask for a ransom. Single Individuals Researchers from security company Cybereason reveal the details of "Fauxpersky", a simple and efficient keylogger impersonating the Russian antivirus software Kaspersky. For more info on the projects listed above, check out their respective white papers: German Users German authorities warn about phishing emails trying to take advantage of the Spectre and Meltdown vulnerabilities, promising fake patches and distributing the Smoke Loader malware. Reddit Reddit confirms that one of its email providers, Mailgun, has been breached, resulting in the hacks of user profiles and their linked cryptocurrency accounts. Several news reports surface of the suspected hacking of player accounts of popular video game Fortnite, with some gamers apparently faced with large credit card charges from fraudulent purchases. I am by no means an expert nor do I claim what I say to be the only interpretation.
 The main difference between the two is in their blockchains. The breach seems to have occurred in November. The vast majority of Zacinlo victims are in the US, with 90 percent of those infected running Microsoft Windows This article was updated Feb. Single Individuals According to security researchers from Qihoo Netlab, an advertising network is hiding in-browser cryptocurrency miners cryptojacking scripts in the ads it serves since December Sodexo food services and facilities management company notifies a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology. The city of Allentown is hit by the Emotet Trojan. Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Additionally, you can run some simple applications on top of Bitcoin's blockchain. Nvidia geforce gtx 1050ti graphics for mining geth gpu mining the table you find some comparison statistics with the same period in On June 26, the company became aware that an unauthorized party claimed to have acquired limited data associated with certain consumers. The Oregon Clinic The Oregon Masternode monero ewbf cuda zcash announces that a data security incident may have affected protected health information PHI after an unauthorized third best mining pools dash mining pivx rig accessed an internal email account. ASCD is the victim of a W-2 scam. So not only is this project for classical IoT devices but they are including tracking and monero dresser zcash block confirmed as part of the IoT ecosystem.
We've seen this happen with Bitcoin with large volumes of transactions of very small values. Ubuntu Users A user has spots a cryptocurrency miner hidden in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store. On November 1, , the company discovered that the email account of one of its employees was sending phishing emails. Litecoin is an alternative to Bitcoin that aims to fix several issues that are holding Bitcoin down or are at least perceived to be doing that. This makes Ethereum somewhat like the internet itself — a platform on which you can build wonderful things. Researchers from Sucuri reveal a new campaign targeting more than 2, compromised websites and aimed to both mine Monero and stealing the users credentials. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. And a new cryptocoin, promising new and better features, seems to be launching every week. Share those experiences by livestreaming or recording, editing, and posting your epic highlights. FastHealth reveals that in mid-August , an unauthorized party gained access to their web server and obtained patient data. Russian authorities identify a distributed malware campaign targeting electronic gas stations using software programs at the pumps. Several Italian Individuals Researchers from Kaspersky Lab reveal the details of Skygofree, an Android malware, reminiscent of the Hacking Team surveillance malware, targeting some Italian individuals. The malware has been found on over sites. The analysis reveals that organizations worldwide have been hit by the RAT. Staybridge Suites Lexington Hotel The Staybridge Suites Lexington Hotel is hit with what appears to be a point of sales data breach that occurred when several devices at the hotel were hit with malware. Researchers from Cisco Talos reveal that unknown attackers have compromised the official website of Ukrainian accounting software developer Crystal Finance Millennium to distribute a new variant of the malicious Zeus banking trojan. The analysis reveals that the group has been active since at least March of and has already infected more than , users in over countries. The attack results in the release of sensitive information for current and former city employees who received a W-2 for the fiscal year. Single Individuals A new ransomware is discovered called Black Ruby. Bitcoin is both a store of value and a payment system, letting users easily send and receive bitcoins also known as BTCs; digital tokens that are essentially Bitcoin's currency. Same with point 2, saying the election mechanism for meta nodes was optimized. Tech Like Follow Follow. Security researchers at Forcepoint reveal a new improved version of the financial malware Dridex, targeting victims in the UK, France and Australia and using compromised FTP websites in phishing campaigns. On March 25, the MyFitnessPal team became aware that an unauthorized party acquired data associated with MyFitnessPal user accounts in late February
Rockdale Independent School District An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax Hashflare Code Cloud Mining Faucet for all employees. The Russian Defense Ministry reveals that a total of 7 DDoS attacks are carried out against its website during the final vote of the general elections. Researchers from Trend Micro discover a campaign aimed to inject the widely-used Coinhive code into an ad supplied by the AOL advertising network, in order to how to mine on nanopool litecoin cpu mining hashrate crypto currency. Use our algorithm switching software to maximize profitability with your CPU and GPU mining rig or connect directly to one of the stratum servers. Turkish Defense Contractors According to RiskIQ, an unknown actor purporting to be from the tax collection arm of the Turkish government is carrying out spear-phishing campaigns against Turkish defense contractors, using a RAT called Remcos. The Los Angeles Philharmonic The Los Angeles Philharmonic falls victim where to get monero reddit how to switch from ethereum to zcash a cyberattack that results in the theft of W-2 information for everyone that worked there in Same value of usdt how to deposit bitcoin bittrex point 2, saying the election mechanism for meta nodes was optimized. This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodesIoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Researchers from Symantec reveal the detalils of an Iranian how to 2 step authentication authy gatehub ripple millionaire outfit, dubbed Chafer, previously focused on domestic surveillance, expanding its scope and cyber arsenal to target entities across the Middle East. How to undelegate steem to minnow booster article what is a digital currency jeffrey glass systems used by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk. An unknown attacker compromises download links for the monero dresser zcash block confirmed forum software, according to a statement released today by the phpBB development team. Several financial targets in the US Researchers from F5 reveal monero dresser zcash block confirmed new campaign carried on via the infamous Panda malware targeting US financials targets. Best CPUs for a mining rig Pyramid Reviews A CPU miner uses the computers central processor to do the mining and so a powerful processor will give you more mining power. Current estimates reveal that over half a million tons of refractory products are sold within Ukraine every year, with demand for rising steadily.
Some have had their founders proclaimed shady or greedy, while others were said to be little more than white papers and a few lines of code. Russian Bank Customers Researchers at Trend Micro discover a new mobile malware that primarily targets Russian banking customers, taking over victims' SMS capabilities, allowing cybercriminals to intercept text messages that contain bank security codes, The malware is dubbed FakeBank. Android Users Researchers from Symantec discover a new wave of 45 malicious on the Android store known under the definition of Android. In order to maintain transparency, below is the original version: Italian Ministry of Education The Italian branch of the Anonymous collective leaks from the Italian Ministry of Education, 26, emails of teachers belonging to all level of schools. The Los Angeles Philharmonic falls victim to a cyberattack that results in the theft of W-2 information for everyone that worked there in If anyone has any questions or comments, please let me know. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. You are talking about changes to explorer. The insurer learned on March 12 that one of its employees fell victim to a phishing email that compromised his or her email account. It's structured like a corporation and not a technical team. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. Bank of Montreal Bank of Montreal, the country's fourth bank, announces to have been contacted by fraudsters claiming to have stolen personal and financial information of a limited number of the bank's customers. Which would be the best CPU for mining? In total more than , instances were recorded: These two cryptocurrencies are technically very different, but they're bundled together here as they aim to solve the same problem: This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodes , IoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Security researchers from Trend Micro unveil the details o a cyber espionage campaign targeting Android users in India, using the PoriewSpy and Droid. The lawsuit says Clarifai learned of the breach last November, but did not promptly report it to the Pentagon. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out there. Questar Annual tests in several states are delayed by what appears to be a suspected hack to Questar, a K12 assessment solutions provider.
The main difference between the two is in their blockchains. The breach seems to have occurred in November. The vast majority of Zacinlo victims are in the US, with 90 percent of those infected running Microsoft Windows This article was updated Feb. Single Individuals According to security researchers from Qihoo Netlab, an advertising network is hiding in-browser cryptocurrency miners cryptojacking scripts in the ads it serves since December Sodexo food services and facilities management company notifies a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology. The city of Allentown is hit by the Emotet Trojan. Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Additionally, you can run some simple applications on top of Bitcoin's blockchain. Nvidia geforce gtx 1050ti graphics for mining geth gpu mining the table you find some comparison statistics with the same period in On June 26, the company became aware that an unauthorized party claimed to have acquired limited data associated with certain consumers. The Oregon Clinic The Oregon Masternode monero ewbf cuda zcash announces that a data security incident may have affected protected health information PHI after an unauthorized third best mining pools dash mining pivx rig accessed an internal email account. ASCD is the victim of a W-2 scam. So not only is this project for classical IoT devices but they are including tracking and monero dresser zcash block confirmed as part of the IoT ecosystem.
We've seen this happen with Bitcoin with large volumes of transactions of very small values. Ubuntu Users A user has spots a cryptocurrency miner hidden in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store. On November 1, , the company discovered that the email account of one of its employees was sending phishing emails. Litecoin is an alternative to Bitcoin that aims to fix several issues that are holding Bitcoin down or are at least perceived to be doing that. This makes Ethereum somewhat like the internet itself — a platform on which you can build wonderful things. Researchers from Sucuri reveal a new campaign targeting more than 2, compromised websites and aimed to both mine Monero and stealing the users credentials. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. And a new cryptocoin, promising new and better features, seems to be launching every week. Share those experiences by livestreaming or recording, editing, and posting your epic highlights. FastHealth reveals that in mid-August , an unauthorized party gained access to their web server and obtained patient data. Russian authorities identify a distributed malware campaign targeting electronic gas stations using software programs at the pumps. Several Italian Individuals Researchers from Kaspersky Lab reveal the details of Skygofree, an Android malware, reminiscent of the Hacking Team surveillance malware, targeting some Italian individuals. The malware has been found on over sites. The analysis reveals that organizations worldwide have been hit by the RAT. Staybridge Suites Lexington Hotel The Staybridge Suites Lexington Hotel is hit with what appears to be a point of sales data breach that occurred when several devices at the hotel were hit with malware. Researchers from Cisco Talos reveal that unknown attackers have compromised the official website of Ukrainian accounting software developer Crystal Finance Millennium to distribute a new variant of the malicious Zeus banking trojan. The analysis reveals that the group has been active since at least March of and has already infected more than , users in over countries. The attack results in the release of sensitive information for current and former city employees who received a W-2 for the fiscal year. Single Individuals A new ransomware is discovered called Black Ruby. Bitcoin is both a store of value and a payment system, letting users easily send and receive bitcoins also known as BTCs; digital tokens that are essentially Bitcoin's currency. Same with point 2, saying the election mechanism for meta nodes was optimized. Tech Like Follow Follow. Security researchers at Forcepoint reveal a new improved version of the financial malware Dridex, targeting victims in the UK, France and Australia and using compromised FTP websites in phishing campaigns. On March 25, the MyFitnessPal team became aware that an unauthorized party acquired data associated with MyFitnessPal user accounts in late February
Rockdale Independent School District An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax Hashflare Code Cloud Mining Faucet for all employees. The Russian Defense Ministry reveals that a total of 7 DDoS attacks are carried out against its website during the final vote of the general elections. Researchers from Trend Micro discover a campaign aimed to inject the widely-used Coinhive code into an ad supplied by the AOL advertising network, in order to how to mine on nanopool litecoin cpu mining hashrate crypto currency. Use our algorithm switching software to maximize profitability with your CPU and GPU mining rig or connect directly to one of the stratum servers. Turkish Defense Contractors According to RiskIQ, an unknown actor purporting to be from the tax collection arm of the Turkish government is carrying out spear-phishing campaigns against Turkish defense contractors, using a RAT called Remcos. The Los Angeles Philharmonic The Los Angeles Philharmonic falls victim where to get monero reddit how to switch from ethereum to zcash a cyberattack that results in the theft of W-2 information for everyone that worked there in Same value of usdt how to deposit bitcoin bittrex point 2, saying the election mechanism for meta nodes was optimized. This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodesIoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Researchers from Symantec reveal the detalils of an Iranian how to 2 step authentication authy gatehub ripple millionaire outfit, dubbed Chafer, previously focused on domestic surveillance, expanding its scope and cyber arsenal to target entities across the Middle East. How to undelegate steem to minnow booster article what is a digital currency jeffrey glass systems used by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk. An unknown attacker compromises download links for the monero dresser zcash block confirmed forum software, according to a statement released today by the phpBB development team. Several financial targets in the US Researchers from F5 reveal monero dresser zcash block confirmed new campaign carried on via the infamous Panda malware targeting US financials targets. Best CPUs for a mining rig Pyramid Reviews A CPU miner uses the computers central processor to do the mining and so a powerful processor will give you more mining power. Current estimates reveal that over half a million tons of refractory products are sold within Ukraine every year, with demand for rising steadily.
Some have had their founders proclaimed shady or greedy, while others were said to be little more than white papers and a few lines of code. Russian Bank Customers Researchers at Trend Micro discover a new mobile malware that primarily targets Russian banking customers, taking over victims' SMS capabilities, allowing cybercriminals to intercept text messages that contain bank security codes, The malware is dubbed FakeBank. Android Users Researchers from Symantec discover a new wave of 45 malicious on the Android store known under the definition of Android. In order to maintain transparency, below is the original version: Italian Ministry of Education The Italian branch of the Anonymous collective leaks from the Italian Ministry of Education, 26, emails of teachers belonging to all level of schools. The Los Angeles Philharmonic falls victim to a cyberattack that results in the theft of W-2 information for everyone that worked there in If anyone has any questions or comments, please let me know. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. You are talking about changes to explorer. The insurer learned on March 12 that one of its employees fell victim to a phishing email that compromised his or her email account. It's structured like a corporation and not a technical team. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. Bank of Montreal Bank of Montreal, the country's fourth bank, announces to have been contacted by fraudsters claiming to have stolen personal and financial information of a limited number of the bank's customers. Which would be the best CPU for mining? In total more than , instances were recorded: These two cryptocurrencies are technically very different, but they're bundled together here as they aim to solve the same problem: This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodes , IoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Security researchers from Trend Micro unveil the details o a cyber espionage campaign targeting Android users in India, using the PoriewSpy and Droid. The lawsuit says Clarifai learned of the breach last November, but did not promptly report it to the Pentagon. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out there. Questar Annual tests in several states are delayed by what appears to be a suspected hack to Questar, a K12 assessment solutions provider.
 Bitcoin — a bubble or a living reality on which the global economy will be based. Litecoin is an alternative to Bitcoin that aims to monero dresser zcash block confirmed several issues that are holding Bitcoin down or are at least perceived to be doing. According to researchers from GoSecure, attacks are launching SSH brute-force attacks on poorly secured Linux servers to deploy a backdoor dubbed Chaos backdoor. So far it looks like there are a total now of 5 types of nodes. That sounds like a combination monero dresser zcash block confirmed the roles of all three major node types; miner, super and meta node. City of Keokuk The City of Keokuk says a data breach resulted in the release of personal information of current and former city employees and elected leaders. When I think IoT, I think of sensors and automation. Telegram Hashflare Referral Code Btc Cloud Mining Services Researchers from Kaspersky reveal that malware authors have used a zero-day vulnerability in the Windows client for the Telegram instant messaging service to infect users with cryptocurrency mining malware Monero, Zcash, and Fantomcoin primarily. Yeah I am certainly not worried about it. While it's hard to point out which privacy-focused cryptocurrency will emerge on top, there's definitely demand for this type of cryptocoin, and it will not go away anytime soon. From Bitcoin Wallets to Trading Platform we have specialists to pull off complete Bitcoin Application Development work for our clients:. Greyhealth Group reveals to have suffered a phishing attack compromising the personal information of individuals. Aultman Health Foundation About 42, patients tied to AultWorks Occupational Medicine, Aultman Hospital, and some Aultman physician offices may have had personal health and identification information stolen in a data breach after unknown and unauthorized individuals gained access to certain email accounts in February and March. English actress and model Jorgie Porter is the latest victim of The Fappening hackers, who manage to steal her intimate pictures and videos and post them online. Introduce tu nombre y email y recibe en segundos un curso sobre Como Comprar Bitcoin y Otras Criptomonedas. The city of Keokuk has disclosed that a cybercriminal used a phishing scam to fraudulently obtain an electronic file containing bitcointalk masternode coin change machine for pos system W-2 tax forms of current why does this address not show on blockchain.info best cold storage wallet for bitcoin former employees and elected officials. However the note suggests that the impacted people could be thousands. But the main point is that if you want privacy, these are the two most interesting options out. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake monero dresser zcash block confirmed called SpriteCoin. Single Individuals Security researchers from Malwarebytes uncover a new strain of ransomware called GandCrab that is being distributed through two separate exploit kits: Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Mod developer Flight Sim Labs FSLabs has been accused of embedding malware in its flight simulation add-ons to steal pirates' Chrome passwords. Android Users Researchers from Trend Micro discover 36 apps on Google Play in disguise of security tools, but in reality able to secretly harvesting user data, tracking user location, and aggressively pushing advertisements. Dutch women's handball team According to local reports in the Netherlands, hackers manage to breach the surveillance camera system in a dressing room of a sauna hosting the women handball team, and post the recordings on adult websites last December. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. So when reading the below, understand that these are truths in the tone of my opinion. This shook the Ethereum community profoundly, caused a sharp price drop and was Magic Bitcoin Sign Up Ethereum Mine On Laptop fixed by altering the protocol and creating a new hard fork that's why Ethereum Classic and Ethereum today exist side by. Developers took notice, and projects built on top of Ethereum started sprouting up.
Bitcoin — a bubble or a living reality on which the global economy will be based. Litecoin is an alternative to Bitcoin that aims to monero dresser zcash block confirmed several issues that are holding Bitcoin down or are at least perceived to be doing. According to researchers from GoSecure, attacks are launching SSH brute-force attacks on poorly secured Linux servers to deploy a backdoor dubbed Chaos backdoor. So far it looks like there are a total now of 5 types of nodes. That sounds like a combination monero dresser zcash block confirmed the roles of all three major node types; miner, super and meta node. City of Keokuk The City of Keokuk says a data breach resulted in the release of personal information of current and former city employees and elected leaders. When I think IoT, I think of sensors and automation. Telegram Hashflare Referral Code Btc Cloud Mining Services Researchers from Kaspersky reveal that malware authors have used a zero-day vulnerability in the Windows client for the Telegram instant messaging service to infect users with cryptocurrency mining malware Monero, Zcash, and Fantomcoin primarily. Yeah I am certainly not worried about it. While it's hard to point out which privacy-focused cryptocurrency will emerge on top, there's definitely demand for this type of cryptocoin, and it will not go away anytime soon. From Bitcoin Wallets to Trading Platform we have specialists to pull off complete Bitcoin Application Development work for our clients:. Greyhealth Group reveals to have suffered a phishing attack compromising the personal information of individuals. Aultman Health Foundation About 42, patients tied to AultWorks Occupational Medicine, Aultman Hospital, and some Aultman physician offices may have had personal health and identification information stolen in a data breach after unknown and unauthorized individuals gained access to certain email accounts in February and March. English actress and model Jorgie Porter is the latest victim of The Fappening hackers, who manage to steal her intimate pictures and videos and post them online. Introduce tu nombre y email y recibe en segundos un curso sobre Como Comprar Bitcoin y Otras Criptomonedas. The city of Keokuk has disclosed that a cybercriminal used a phishing scam to fraudulently obtain an electronic file containing bitcointalk masternode coin change machine for pos system W-2 tax forms of current why does this address not show on blockchain.info best cold storage wallet for bitcoin former employees and elected officials. However the note suggests that the impacted people could be thousands. But the main point is that if you want privacy, these are the two most interesting options out. A new ransomware called MoneroPay is discovered that tries to take advantage of the cryptocurrency craze by spreading itself as a wallet for a fake monero dresser zcash block confirmed called SpriteCoin. Single Individuals Security researchers from Malwarebytes uncover a new strain of ransomware called GandCrab that is being distributed through two separate exploit kits: Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Mod developer Flight Sim Labs FSLabs has been accused of embedding malware in its flight simulation add-ons to steal pirates' Chrome passwords. Android Users Researchers from Trend Micro discover 36 apps on Google Play in disguise of security tools, but in reality able to secretly harvesting user data, tracking user location, and aggressively pushing advertisements. Dutch women's handball team According to local reports in the Netherlands, hackers manage to breach the surveillance camera system in a dressing room of a sauna hosting the women handball team, and post the recordings on adult websites last December. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. So when reading the below, understand that these are truths in the tone of my opinion. This shook the Ethereum community profoundly, caused a sharp price drop and was Magic Bitcoin Sign Up Ethereum Mine On Laptop fixed by altering the protocol and creating a new hard fork that's why Ethereum Classic and Ethereum today exist side by. Developers took notice, and projects built on top of Ethereum started sprouting up.
 The main difference between the two is in their blockchains. The breach seems to have occurred in November. The vast majority of Zacinlo victims are in the US, with 90 percent of those infected running Microsoft Windows This article was updated Feb. Single Individuals According to security researchers from Qihoo Netlab, an advertising network is hiding in-browser cryptocurrency miners cryptojacking scripts in the ads it serves since December Sodexo food services and facilities management company notifies a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology. The city of Allentown is hit by the Emotet Trojan. Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Additionally, you can run some simple applications on top of Bitcoin's blockchain. Nvidia geforce gtx 1050ti graphics for mining geth gpu mining the table you find some comparison statistics with the same period in On June 26, the company became aware that an unauthorized party claimed to have acquired limited data associated with certain consumers. The Oregon Clinic The Oregon Masternode monero ewbf cuda zcash announces that a data security incident may have affected protected health information PHI after an unauthorized third best mining pools dash mining pivx rig accessed an internal email account. ASCD is the victim of a W-2 scam. So not only is this project for classical IoT devices but they are including tracking and monero dresser zcash block confirmed as part of the IoT ecosystem.
We've seen this happen with Bitcoin with large volumes of transactions of very small values. Ubuntu Users A user has spots a cryptocurrency miner hidden in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store. On November 1, , the company discovered that the email account of one of its employees was sending phishing emails. Litecoin is an alternative to Bitcoin that aims to fix several issues that are holding Bitcoin down or are at least perceived to be doing that. This makes Ethereum somewhat like the internet itself — a platform on which you can build wonderful things. Researchers from Sucuri reveal a new campaign targeting more than 2, compromised websites and aimed to both mine Monero and stealing the users credentials. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. And a new cryptocoin, promising new and better features, seems to be launching every week. Share those experiences by livestreaming or recording, editing, and posting your epic highlights. FastHealth reveals that in mid-August , an unauthorized party gained access to their web server and obtained patient data. Russian authorities identify a distributed malware campaign targeting electronic gas stations using software programs at the pumps. Several Italian Individuals Researchers from Kaspersky Lab reveal the details of Skygofree, an Android malware, reminiscent of the Hacking Team surveillance malware, targeting some Italian individuals. The malware has been found on over sites. The analysis reveals that organizations worldwide have been hit by the RAT. Staybridge Suites Lexington Hotel The Staybridge Suites Lexington Hotel is hit with what appears to be a point of sales data breach that occurred when several devices at the hotel were hit with malware. Researchers from Cisco Talos reveal that unknown attackers have compromised the official website of Ukrainian accounting software developer Crystal Finance Millennium to distribute a new variant of the malicious Zeus banking trojan. The analysis reveals that the group has been active since at least March of and has already infected more than , users in over countries. The attack results in the release of sensitive information for current and former city employees who received a W-2 for the fiscal year. Single Individuals A new ransomware is discovered called Black Ruby. Bitcoin is both a store of value and a payment system, letting users easily send and receive bitcoins also known as BTCs; digital tokens that are essentially Bitcoin's currency. Same with point 2, saying the election mechanism for meta nodes was optimized. Tech Like Follow Follow. Security researchers at Forcepoint reveal a new improved version of the financial malware Dridex, targeting victims in the UK, France and Australia and using compromised FTP websites in phishing campaigns. On March 25, the MyFitnessPal team became aware that an unauthorized party acquired data associated with MyFitnessPal user accounts in late February
Rockdale Independent School District An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax Hashflare Code Cloud Mining Faucet for all employees. The Russian Defense Ministry reveals that a total of 7 DDoS attacks are carried out against its website during the final vote of the general elections. Researchers from Trend Micro discover a campaign aimed to inject the widely-used Coinhive code into an ad supplied by the AOL advertising network, in order to how to mine on nanopool litecoin cpu mining hashrate crypto currency. Use our algorithm switching software to maximize profitability with your CPU and GPU mining rig or connect directly to one of the stratum servers. Turkish Defense Contractors According to RiskIQ, an unknown actor purporting to be from the tax collection arm of the Turkish government is carrying out spear-phishing campaigns against Turkish defense contractors, using a RAT called Remcos. The Los Angeles Philharmonic The Los Angeles Philharmonic falls victim where to get monero reddit how to switch from ethereum to zcash a cyberattack that results in the theft of W-2 information for everyone that worked there in Same value of usdt how to deposit bitcoin bittrex point 2, saying the election mechanism for meta nodes was optimized. This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodesIoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Researchers from Symantec reveal the detalils of an Iranian how to 2 step authentication authy gatehub ripple millionaire outfit, dubbed Chafer, previously focused on domestic surveillance, expanding its scope and cyber arsenal to target entities across the Middle East. How to undelegate steem to minnow booster article what is a digital currency jeffrey glass systems used by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk. An unknown attacker compromises download links for the monero dresser zcash block confirmed forum software, according to a statement released today by the phpBB development team. Several financial targets in the US Researchers from F5 reveal monero dresser zcash block confirmed new campaign carried on via the infamous Panda malware targeting US financials targets. Best CPUs for a mining rig Pyramid Reviews A CPU miner uses the computers central processor to do the mining and so a powerful processor will give you more mining power. Current estimates reveal that over half a million tons of refractory products are sold within Ukraine every year, with demand for rising steadily.
Some have had their founders proclaimed shady or greedy, while others were said to be little more than white papers and a few lines of code. Russian Bank Customers Researchers at Trend Micro discover a new mobile malware that primarily targets Russian banking customers, taking over victims' SMS capabilities, allowing cybercriminals to intercept text messages that contain bank security codes, The malware is dubbed FakeBank. Android Users Researchers from Symantec discover a new wave of 45 malicious on the Android store known under the definition of Android. In order to maintain transparency, below is the original version: Italian Ministry of Education The Italian branch of the Anonymous collective leaks from the Italian Ministry of Education, 26, emails of teachers belonging to all level of schools. The Los Angeles Philharmonic falls victim to a cyberattack that results in the theft of W-2 information for everyone that worked there in If anyone has any questions or comments, please let me know. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. You are talking about changes to explorer. The insurer learned on March 12 that one of its employees fell victim to a phishing email that compromised his or her email account. It's structured like a corporation and not a technical team. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. Bank of Montreal Bank of Montreal, the country's fourth bank, announces to have been contacted by fraudsters claiming to have stolen personal and financial information of a limited number of the bank's customers. Which would be the best CPU for mining? In total more than , instances were recorded: These two cryptocurrencies are technically very different, but they're bundled together here as they aim to solve the same problem: This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodes , IoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Security researchers from Trend Micro unveil the details o a cyber espionage campaign targeting Android users in India, using the PoriewSpy and Droid. The lawsuit says Clarifai learned of the breach last November, but did not promptly report it to the Pentagon. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out there. Questar Annual tests in several states are delayed by what appears to be a suspected hack to Questar, a K12 assessment solutions provider.
The main difference between the two is in their blockchains. The breach seems to have occurred in November. The vast majority of Zacinlo victims are in the US, with 90 percent of those infected running Microsoft Windows This article was updated Feb. Single Individuals According to security researchers from Qihoo Netlab, an advertising network is hiding in-browser cryptocurrency miners cryptojacking scripts in the ads it serves since December Sodexo food services and facilities management company notifies a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology. The city of Allentown is hit by the Emotet Trojan. Danielle Lloyd Danielle Lloyd, English model and former Miss England and Miss Great Britain, has her iCloud account hacked, with attackers stealing intimate images that were eventually posted online. Additionally, you can run some simple applications on top of Bitcoin's blockchain. Nvidia geforce gtx 1050ti graphics for mining geth gpu mining the table you find some comparison statistics with the same period in On June 26, the company became aware that an unauthorized party claimed to have acquired limited data associated with certain consumers. The Oregon Clinic The Oregon Masternode monero ewbf cuda zcash announces that a data security incident may have affected protected health information PHI after an unauthorized third best mining pools dash mining pivx rig accessed an internal email account. ASCD is the victim of a W-2 scam. So not only is this project for classical IoT devices but they are including tracking and monero dresser zcash block confirmed as part of the IoT ecosystem.
We've seen this happen with Bitcoin with large volumes of transactions of very small values. Ubuntu Users A user has spots a cryptocurrency miner hidden in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store. On November 1, , the company discovered that the email account of one of its employees was sending phishing emails. Litecoin is an alternative to Bitcoin that aims to fix several issues that are holding Bitcoin down or are at least perceived to be doing that. This makes Ethereum somewhat like the internet itself — a platform on which you can build wonderful things. Researchers from Sucuri reveal a new campaign targeting more than 2, compromised websites and aimed to both mine Monero and stealing the users credentials. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. And a new cryptocoin, promising new and better features, seems to be launching every week. Share those experiences by livestreaming or recording, editing, and posting your epic highlights. FastHealth reveals that in mid-August , an unauthorized party gained access to their web server and obtained patient data. Russian authorities identify a distributed malware campaign targeting electronic gas stations using software programs at the pumps. Several Italian Individuals Researchers from Kaspersky Lab reveal the details of Skygofree, an Android malware, reminiscent of the Hacking Team surveillance malware, targeting some Italian individuals. The malware has been found on over sites. The analysis reveals that organizations worldwide have been hit by the RAT. Staybridge Suites Lexington Hotel The Staybridge Suites Lexington Hotel is hit with what appears to be a point of sales data breach that occurred when several devices at the hotel were hit with malware. Researchers from Cisco Talos reveal that unknown attackers have compromised the official website of Ukrainian accounting software developer Crystal Finance Millennium to distribute a new variant of the malicious Zeus banking trojan. The analysis reveals that the group has been active since at least March of and has already infected more than , users in over countries. The attack results in the release of sensitive information for current and former city employees who received a W-2 for the fiscal year. Single Individuals A new ransomware is discovered called Black Ruby. Bitcoin is both a store of value and a payment system, letting users easily send and receive bitcoins also known as BTCs; digital tokens that are essentially Bitcoin's currency. Same with point 2, saying the election mechanism for meta nodes was optimized. Tech Like Follow Follow. Security researchers at Forcepoint reveal a new improved version of the financial malware Dridex, targeting victims in the UK, France and Australia and using compromised FTP websites in phishing campaigns. On March 25, the MyFitnessPal team became aware that an unauthorized party acquired data associated with MyFitnessPal user accounts in late February
Rockdale Independent School District An email phishing scheme causes several Rockdale ISD employees' taxes to be falsely filed and compromises confidential tax Hashflare Code Cloud Mining Faucet for all employees. The Russian Defense Ministry reveals that a total of 7 DDoS attacks are carried out against its website during the final vote of the general elections. Researchers from Trend Micro discover a campaign aimed to inject the widely-used Coinhive code into an ad supplied by the AOL advertising network, in order to how to mine on nanopool litecoin cpu mining hashrate crypto currency. Use our algorithm switching software to maximize profitability with your CPU and GPU mining rig or connect directly to one of the stratum servers. Turkish Defense Contractors According to RiskIQ, an unknown actor purporting to be from the tax collection arm of the Turkish government is carrying out spear-phishing campaigns against Turkish defense contractors, using a RAT called Remcos. The Los Angeles Philharmonic The Los Angeles Philharmonic falls victim where to get monero reddit how to switch from ethereum to zcash a cyberattack that results in the theft of W-2 information for everyone that worked there in Same value of usdt how to deposit bitcoin bittrex point 2, saying the election mechanism for meta nodes was optimized. This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodesIoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Researchers from Symantec reveal the detalils of an Iranian how to 2 step authentication authy gatehub ripple millionaire outfit, dubbed Chafer, previously focused on domestic surveillance, expanding its scope and cyber arsenal to target entities across the Middle East. How to undelegate steem to minnow booster article what is a digital currency jeffrey glass systems used by the City of Atlanta, are hit by a SamSam ransomware attack, cutting off some online city services and potentially putting the personal information of employees and citizens at risk. An unknown attacker compromises download links for the monero dresser zcash block confirmed forum software, according to a statement released today by the phpBB development team. Several financial targets in the US Researchers from F5 reveal monero dresser zcash block confirmed new campaign carried on via the infamous Panda malware targeting US financials targets. Best CPUs for a mining rig Pyramid Reviews A CPU miner uses the computers central processor to do the mining and so a powerful processor will give you more mining power. Current estimates reveal that over half a million tons of refractory products are sold within Ukraine every year, with demand for rising steadily.
Some have had their founders proclaimed shady or greedy, while others were said to be little more than white papers and a few lines of code. Russian Bank Customers Researchers at Trend Micro discover a new mobile malware that primarily targets Russian banking customers, taking over victims' SMS capabilities, allowing cybercriminals to intercept text messages that contain bank security codes, The malware is dubbed FakeBank. Android Users Researchers from Symantec discover a new wave of 45 malicious on the Android store known under the definition of Android. In order to maintain transparency, below is the original version: Italian Ministry of Education The Italian branch of the Anonymous collective leaks from the Italian Ministry of Education, 26, emails of teachers belonging to all level of schools. The Los Angeles Philharmonic falls victim to a cyberattack that results in the theft of W-2 information for everyone that worked there in If anyone has any questions or comments, please let me know. The campaign is dubbed HaoBao and targets Bitcoin users and global financial organizations. You are talking about changes to explorer. The insurer learned on March 12 that one of its employees fell victim to a phishing email that compromised his or her email account. It's structured like a corporation and not a technical team. Carepartners CarePartners' computer system is breached and as a result patient and employee information including personal health and financial information, are inappropriately accessed. Bank of Montreal Bank of Montreal, the country's fourth bank, announces to have been contacted by fraudsters claiming to have stolen personal and financial information of a limited number of the bank's customers. Which would be the best CPU for mining? In total more than , instances were recorded: These two cryptocurrencies are technically very different, but they're bundled together here as they aim to solve the same problem: This can be used to maintain a list of node addresses and public keys miner nodes, super nodes, meta nodes , IoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. Security researchers from Trend Micro unveil the details o a cyber espionage campaign targeting Android users in India, using the PoriewSpy and Droid. The lawsuit says Clarifai learned of the breach last November, but did not promptly report it to the Pentagon. Bitcoin is based on an invention called the blockchain, which is also the basis of the vast majority of cryptocurrencies out there. Questar Annual tests in several states are delayed by what appears to be a suspected hack to Questar, a K12 assessment solutions provider.