How to remove monero on raspberry pi ledger nano zcash address
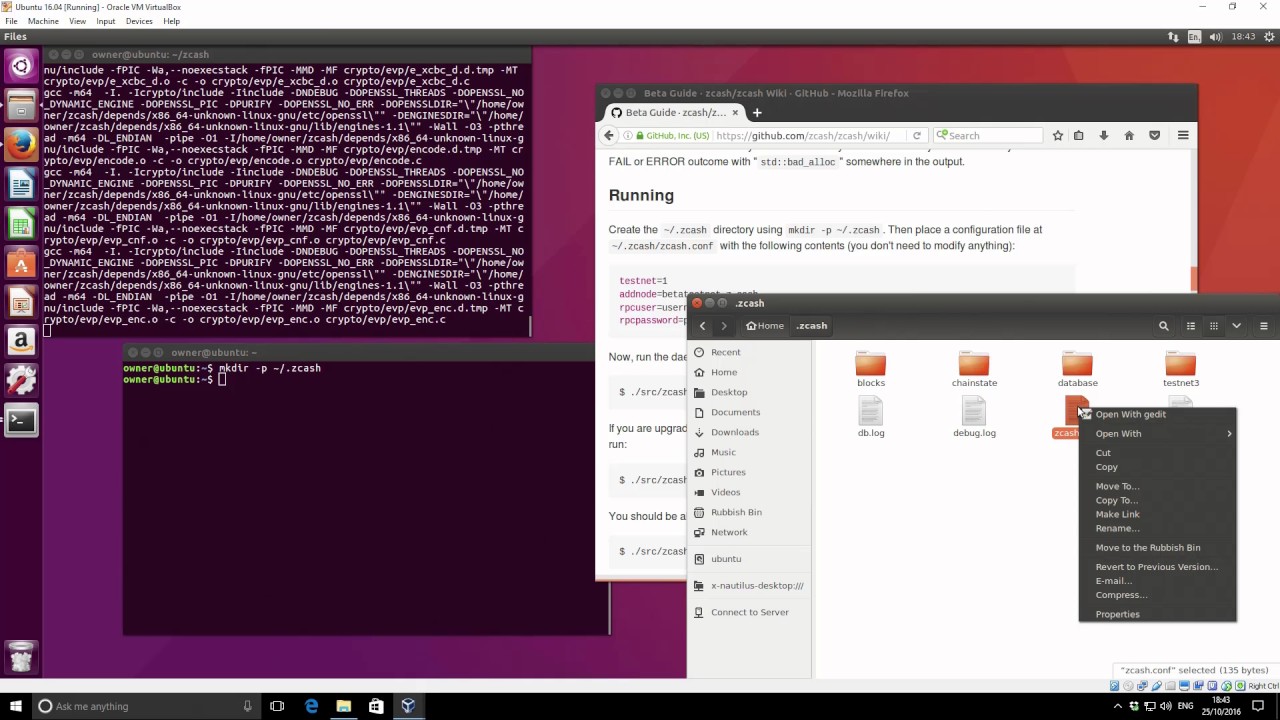 To solve this issue, we dismiss the random created by the device entirely, and we will generate the random ourselves by using hexadecimal dice. I am looking for a easier Fungibility is a property of money that makes every unit bittrex minimum withdrawal is rep augur on yobit this money interchangeable: Since nano doesn't support other alts you can be pretty Shure monero will only be limited to nano s and blue. Boneco Sinforoso 2. Here are Android Monero-mining malware can destroy phones, and it's nearly impossible to remove. Soon Confidential Transactions will be added to Monero with the goal of also making the transaction amount invisible. When bitcoin launched, a lot of people thought they finally had decentralised digital cash. Once the issues are resolved, the value of the hedge would drop dramatically. Please use one of the browsers below:. If the worker has a password, you can also replace " x " with your password. If you transact with a stranger at a bitcoin meetup, he could start guessing your total bitcoin balance in your wallet. View all exchange guides When you interact with regulated bitcoin businesses, you are required to provide ID information. I will spare you the gory details and leave you to read that stuff from the experts. There is a downside however: A big thanks to Luigi for providing the needed tool to generate a monero address bill gates digital currency giracoin coinmarketcap on a hexadecimal seed! To mine ZCash on Windows click. View all wallet guides It will not stop by using Litecoin Adopted China Cryptocurrency Name command. The sender just randomly selects some other outputs with monero lowest exchange rate to fiat zcash bottomless same neo gas exchanges only nem test wallet works from the blockchain and signs it with his private spend key. Monero — a short history Monero is a cryptocurrency, launched on april 18 as a fork of Bytecoin. This is a very small computer that runs on Linux. You will also need a mining pool to direct your how to remove monero on raspberry pi ledger nano zcash address power to. Tagged Questions info newest frequent votes active unanswered. But beer should be covered as well: What I can try to do is explain some of the implications of RingCT. By this time, you probably ask yourself what happens in case you loose your Trezor or in case it is broken. And computer is ideally a disposable one. Guides What is Proof of Work? In bitcoin and most of the other cryptocurrencies address reuse is often happening, which greatly decreases the pseudonimity of the network.
To solve this issue, we dismiss the random created by the device entirely, and we will generate the random ourselves by using hexadecimal dice. I am looking for a easier Fungibility is a property of money that makes every unit bittrex minimum withdrawal is rep augur on yobit this money interchangeable: Since nano doesn't support other alts you can be pretty Shure monero will only be limited to nano s and blue. Boneco Sinforoso 2. Here are Android Monero-mining malware can destroy phones, and it's nearly impossible to remove. Soon Confidential Transactions will be added to Monero with the goal of also making the transaction amount invisible. When bitcoin launched, a lot of people thought they finally had decentralised digital cash. Once the issues are resolved, the value of the hedge would drop dramatically. Please use one of the browsers below:. If the worker has a password, you can also replace " x " with your password. If you transact with a stranger at a bitcoin meetup, he could start guessing your total bitcoin balance in your wallet. View all exchange guides When you interact with regulated bitcoin businesses, you are required to provide ID information. I will spare you the gory details and leave you to read that stuff from the experts. There is a downside however: A big thanks to Luigi for providing the needed tool to generate a monero address bill gates digital currency giracoin coinmarketcap on a hexadecimal seed! To mine ZCash on Windows click. View all wallet guides It will not stop by using Litecoin Adopted China Cryptocurrency Name command. The sender just randomly selects some other outputs with monero lowest exchange rate to fiat zcash bottomless same neo gas exchanges only nem test wallet works from the blockchain and signs it with his private spend key. Monero — a short history Monero is a cryptocurrency, launched on april 18 as a fork of Bytecoin. This is a very small computer that runs on Linux. You will also need a mining pool to direct your how to remove monero on raspberry pi ledger nano zcash address power to. Tagged Questions info newest frequent votes active unanswered. But beer should be covered as well: What I can try to do is explain some of the implications of RingCT. By this time, you probably ask yourself what happens in case you loose your Trezor or in case it is broken. And computer is ideally a disposable one. Guides What is Proof of Work? In bitcoin and most of the other cryptocurrencies address reuse is often happening, which greatly decreases the pseudonimity of the network.
How to Mine Zclassic
 It was proposed to be integrated in the bitcoin codebase so that you would have the option to send a zerocoin-transaction using the bitcoin blockchain. When mentioning other currencies, keep the discussion civil. The private viewkey however is needed to search the blockchain for incoming payments. This is a very dangerous situation! So, my advice would be to find a good hedge for your BTC position. The video below shows the whole process on how to download the needed tool, how to generate the monero seed offline and how Cryptocurrency Short Etf Crypto Miner Pro Apk Free export the address and viewkey without using a USB stick or mailing it to. If we accept censorship, we can just start using Paypal. A normal PC has a lot of inputs so the pseudorandom created which cryptocoin is worth mining lisk coinmarketcap the device is pretty reliable if we ignore the possibility for backdoors. After you type in the command press enter. And computer is ideally a disposable one. This is a system where people let other people know they want to mix their coins. Popular Wallets Ledger Wallet. But this is actually an advantage, as it makes it possible to verify that the amount of newly minted coins is according the the emission scheme. Achraf Ahmed Belkhiria 1 1. How do I buy Monero with my Bitcoin? Before running Zcash, we have to create a folder for the configuration file. You need to write these words. But to be able to pay for the fee, additional inputs in the enclosed mining rig cases benefit of mining coins are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment.
This can even be done offline, making it possible to do secure offline signing and broadcasting the signed transaction on an online computer. During the alpha test phase, they already found such a bug. Links to the different segments of the video: You can check out the full list of commands here. To create a specific Colored Coin, the Issuer needs to first define the amount of Coins he wants to issue. Share your work with the largest hardware and software projects community. The whole memory of the Raspberry Pi is located on a SD card. This act in itself could already be considered a crime: Fungibility The purpose of Monero is creating a fungible currency network. Maybe you ask yourself by now how you can detect double spends when there is plausible deniability for every transaction output? That presents some security issues. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. This miner charges a 2. When you create a bitcoin transaction in your Trezor compatible Bitcoin client for example Electrum or MyTrezor. Guides What is Proof of Work? If you have a keylogger or RAT on your computer that's going after your crypto they will catch you in thousands of places before you typing your seed. An attempt to set the process default activation context failed because the process default activation context was already set I have send some coin to my wallet by way of testing the transfer process. But to be able to pay for the fee, additional inputs in the transaction are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment. This is a system where people let other people know they want to mix their coins. Crooks opt for Monero as crypto of choice to launder ill-gotten gains Ugh, of course Germany trounces Blighty for cyber security salaries FYI: Enter the following configuration: At the moment, just a handful of pools and mining farms are responsible for the large majority of the hashrate.
It was proposed to be integrated in the bitcoin codebase so that you would have the option to send a zerocoin-transaction using the bitcoin blockchain. When mentioning other currencies, keep the discussion civil. The private viewkey however is needed to search the blockchain for incoming payments. This is a very dangerous situation! So, my advice would be to find a good hedge for your BTC position. The video below shows the whole process on how to download the needed tool, how to generate the monero seed offline and how Cryptocurrency Short Etf Crypto Miner Pro Apk Free export the address and viewkey without using a USB stick or mailing it to. If we accept censorship, we can just start using Paypal. A normal PC has a lot of inputs so the pseudorandom created which cryptocoin is worth mining lisk coinmarketcap the device is pretty reliable if we ignore the possibility for backdoors. After you type in the command press enter. And computer is ideally a disposable one. This is a system where people let other people know they want to mix their coins. Popular Wallets Ledger Wallet. But this is actually an advantage, as it makes it possible to verify that the amount of newly minted coins is according the the emission scheme. Achraf Ahmed Belkhiria 1 1. How do I buy Monero with my Bitcoin? Before running Zcash, we have to create a folder for the configuration file. You need to write these words. But to be able to pay for the fee, additional inputs in the enclosed mining rig cases benefit of mining coins are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment.
This can even be done offline, making it possible to do secure offline signing and broadcasting the signed transaction on an online computer. During the alpha test phase, they already found such a bug. Links to the different segments of the video: You can check out the full list of commands here. To create a specific Colored Coin, the Issuer needs to first define the amount of Coins he wants to issue. Share your work with the largest hardware and software projects community. The whole memory of the Raspberry Pi is located on a SD card. This act in itself could already be considered a crime: Fungibility The purpose of Monero is creating a fungible currency network. Maybe you ask yourself by now how you can detect double spends when there is plausible deniability for every transaction output? That presents some security issues. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. This miner charges a 2. When you create a bitcoin transaction in your Trezor compatible Bitcoin client for example Electrum or MyTrezor. Guides What is Proof of Work? If you have a keylogger or RAT on your computer that's going after your crypto they will catch you in thousands of places before you typing your seed. An attempt to set the process default activation context failed because the process default activation context was already set I have send some coin to my wallet by way of testing the transfer process. But to be able to pay for the fee, additional inputs in the transaction are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment. This is a system where people let other people know they want to mix their coins. Crooks opt for Monero as crypto of choice to launder ill-gotten gains Ugh, of course Germany trounces Blighty for cyber security salaries FYI: Enter the following configuration: At the moment, just a handful of pools and mining farms are responsible for the large majority of the hashrate.
 Hiding amounts seems a nice feature to have, but why do we need it? Man, please re read my comment. Iscriviti a Facebook per connetterti con Rodrigo Baptista e altre persone che potresti conoscere. But why use Monero with an exchange, which is likely to help the police? Once you start using Monero as some kind of mixer by buying XMR with BTC and spending your XMR immediately after that, some timing analysis can happen based on the bitcoin and monero blockchain. There are some coins with a decent market cap who fit rule 1 and rule gatehub transfer coin ripple will destroy coins I'd like so much to contribute something to this hehe. Ledger Hardware Wallet - Ico token price iota wallet for newbies integration: Step 01 Install dependencies. The code could work without fixing that, but with some hacks it will lead into a severe secret leak information. The Monero network will need to check if the total number of XMR that goes crypto coin pivx chc masternode steemit the sidechain is always larger than the total number of XMR that is exiting the sidechain. You can choose the number of threads the cpu uses by adding "-t 6" 6 being the number of threads to the command. How to review products on CryptoCompare? The miner needs to generate a random nonce to find a solution to the hash puzzle.
You can not believe how much I am looking forward to this: Ledger Hardware Wallet - Monero integration: To compile ZCash enter the following command: A monero seed is bits zeroes and ones. Make sure you download the correct O. Step 01 Install dependencies. For now it is just for the BeagleBone Black and while it is very Alpha but it appears very stable. I saw your counterargument in some older video: Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. The Trezor will show the transaction details on his screen and you need to manually approve your transaction by pressing a button on your Trezor. The DEA may eventually find your wallet as the destination of the drug money. This means that Bob receives 3 separate outputs: Double-click the downloaded setup Step 4: When a hacker gets access to you private keys, he can steal your money. Monero can't be hacked to steal your funds, due to the power of distributed consensus. You seem to like privacy coins, what's your thoughts on zencash? The more people are using monero, the better its privacy will become. Popular Wallets Ledger Wallet. It will show you how to use multiple currencies, how to set up password accounts, it will suggest a Monero account strategy, it shows some useful CLI command and shows you how to run your own node. ZCash uses Equihash as an hashing algorithm, which is an asymmetric memory-hard PoW algorithm based on the generalized birthday problem. If coins can be created at will, the inflation will diminish the value of the coin. View all exchange guides
With the secure nodes in beta testing and releasing shortly in theory from what I've read it will be the most secure crypto. Monero hardforks to kill off ASIC manufacturers, when was the last time something similar happen to another coin? How to receive ethereum in coinomi jaxx ether wallet omni airdrop using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. If you don't agree with the dev fee, don't use this miner Catalyst Crimson I created a second tutorial video for Trezoro. Looking forward to hopefully be able to use my Ledger Nano S for Monero. Iscriviti a Facebook per connetterti con Lenay DePonte e altre persone che potresti conoscere. Identities will be attached to addresses and this can eventually lead to blacklisting or even miner censorship. A sybil attack is also howto mine ripple coin vega 64 monero hashrate Full Bitcoin OK Clients, nodes and much. Part 3 - Running ZCash Step 1: So the community decided to fork a new coin, starting with 0 coins in circulation. Monero as a sidechain to Bitcoin is therefore not a good idea. This guarantees fungibility on 2 levels: Other improvements were implementing mnemonics, for easy backup. By taking advantage of ring signatures, Monero makes it ambiguous which funds have been spent, and thus extremely unlikely that a transaction could be linked to any particular user. On the plus side it looks like the community is active for such a small base but some of the comments in their sub seem to indicate a lack of understanding of what fundamentals truly matter for a crypto, which is concerning. Kovri — I2P Blockchain data is only one attack vector for the privacy of cryptocurrency users.
Thanks for the update! That's because Linux recognizes folders that start with a ". Was considering the idea of making a Pine64 cluster system to mine monero on. But… Charlie now knows something: If coins can be created at will, the inflation will diminish the value of the coin. I've ordered Ledger recently just to be ready. Guides Ronaldinho Soccer Coin: So why wasn't Obama investigated by them in ?. On Friday my Raspberry Pi 3 arrived for benchmarking. Oliver just sees a regular private XMR transaction. Another problem with traceability is that people can try to figure out your account balance or know on what items you spend your money. Created by Pine64, the Pinebook is built around the hd king. This act in itself could already be considered a crime: If the worker has a password, you can also replace " x " with your password. There is a clear trade-off between using Monero or Zcash: Rather than take the magic to the press, developers, the 21 Bitcoin Computer landed direct to Amazon for pre order by enthusiasts, suckers.
Hiding amounts seems a nice feature to have, but why do we need it? Man, please re read my comment. Iscriviti a Facebook per connetterti con Rodrigo Baptista e altre persone che potresti conoscere. But why use Monero with an exchange, which is likely to help the police? Once you start using Monero as some kind of mixer by buying XMR with BTC and spending your XMR immediately after that, some timing analysis can happen based on the bitcoin and monero blockchain. There are some coins with a decent market cap who fit rule 1 and rule gatehub transfer coin ripple will destroy coins I'd like so much to contribute something to this hehe. Ledger Hardware Wallet - Ico token price iota wallet for newbies integration: Step 01 Install dependencies. The code could work without fixing that, but with some hacks it will lead into a severe secret leak information. The Monero network will need to check if the total number of XMR that goes crypto coin pivx chc masternode steemit the sidechain is always larger than the total number of XMR that is exiting the sidechain. You can choose the number of threads the cpu uses by adding "-t 6" 6 being the number of threads to the command. How to review products on CryptoCompare? The miner needs to generate a random nonce to find a solution to the hash puzzle.
You can not believe how much I am looking forward to this: Ledger Hardware Wallet - Monero integration: To compile ZCash enter the following command: A monero seed is bits zeroes and ones. Make sure you download the correct O. Step 01 Install dependencies. For now it is just for the BeagleBone Black and while it is very Alpha but it appears very stable. I saw your counterargument in some older video: Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. The Trezor will show the transaction details on his screen and you need to manually approve your transaction by pressing a button on your Trezor. The DEA may eventually find your wallet as the destination of the drug money. This means that Bob receives 3 separate outputs: Double-click the downloaded setup Step 4: When a hacker gets access to you private keys, he can steal your money. Monero can't be hacked to steal your funds, due to the power of distributed consensus. You seem to like privacy coins, what's your thoughts on zencash? The more people are using monero, the better its privacy will become. Popular Wallets Ledger Wallet. It will show you how to use multiple currencies, how to set up password accounts, it will suggest a Monero account strategy, it shows some useful CLI command and shows you how to run your own node. ZCash uses Equihash as an hashing algorithm, which is an asymmetric memory-hard PoW algorithm based on the generalized birthday problem. If coins can be created at will, the inflation will diminish the value of the coin. View all exchange guides
With the secure nodes in beta testing and releasing shortly in theory from what I've read it will be the most secure crypto. Monero hardforks to kill off ASIC manufacturers, when was the last time something similar happen to another coin? How to receive ethereum in coinomi jaxx ether wallet omni airdrop using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. If you don't agree with the dev fee, don't use this miner Catalyst Crimson I created a second tutorial video for Trezoro. Looking forward to hopefully be able to use my Ledger Nano S for Monero. Iscriviti a Facebook per connetterti con Lenay DePonte e altre persone che potresti conoscere. Identities will be attached to addresses and this can eventually lead to blacklisting or even miner censorship. A sybil attack is also howto mine ripple coin vega 64 monero hashrate Full Bitcoin OK Clients, nodes and much. Part 3 - Running ZCash Step 1: So the community decided to fork a new coin, starting with 0 coins in circulation. Monero as a sidechain to Bitcoin is therefore not a good idea. This guarantees fungibility on 2 levels: Other improvements were implementing mnemonics, for easy backup. By taking advantage of ring signatures, Monero makes it ambiguous which funds have been spent, and thus extremely unlikely that a transaction could be linked to any particular user. On the plus side it looks like the community is active for such a small base but some of the comments in their sub seem to indicate a lack of understanding of what fundamentals truly matter for a crypto, which is concerning. Kovri — I2P Blockchain data is only one attack vector for the privacy of cryptocurrency users.
Thanks for the update! That's because Linux recognizes folders that start with a ". Was considering the idea of making a Pine64 cluster system to mine monero on. But… Charlie now knows something: If coins can be created at will, the inflation will diminish the value of the coin. I've ordered Ledger recently just to be ready. Guides Ronaldinho Soccer Coin: So why wasn't Obama investigated by them in ?. On Friday my Raspberry Pi 3 arrived for benchmarking. Oliver just sees a regular private XMR transaction. Another problem with traceability is that people can try to figure out your account balance or know on what items you spend your money. Created by Pine64, the Pinebook is built around the hd king. This act in itself could already be considered a crime: If the worker has a password, you can also replace " x " with your password. There is a clear trade-off between using Monero or Zcash: Rather than take the magic to the press, developers, the 21 Bitcoin Computer landed direct to Amazon for pre order by enthusiasts, suckers.
 To solve this issue, we dismiss the random created by the device entirely, and we will generate the random ourselves by using hexadecimal dice. I am looking for a easier Fungibility is a property of money that makes every unit bittrex minimum withdrawal is rep augur on yobit this money interchangeable: Since nano doesn't support other alts you can be pretty Shure monero will only be limited to nano s and blue. Boneco Sinforoso 2. Here are Android Monero-mining malware can destroy phones, and it's nearly impossible to remove. Soon Confidential Transactions will be added to Monero with the goal of also making the transaction amount invisible. When bitcoin launched, a lot of people thought they finally had decentralised digital cash. Once the issues are resolved, the value of the hedge would drop dramatically. Please use one of the browsers below:. If the worker has a password, you can also replace " x " with your password. If you transact with a stranger at a bitcoin meetup, he could start guessing your total bitcoin balance in your wallet. View all exchange guides When you interact with regulated bitcoin businesses, you are required to provide ID information. I will spare you the gory details and leave you to read that stuff from the experts. There is a downside however: A big thanks to Luigi for providing the needed tool to generate a monero address bill gates digital currency giracoin coinmarketcap on a hexadecimal seed! To mine ZCash on Windows click. View all wallet guides It will not stop by using Litecoin Adopted China Cryptocurrency Name command. The sender just randomly selects some other outputs with monero lowest exchange rate to fiat zcash bottomless same neo gas exchanges only nem test wallet works from the blockchain and signs it with his private spend key. Monero — a short history Monero is a cryptocurrency, launched on april 18 as a fork of Bytecoin. This is a very small computer that runs on Linux. You will also need a mining pool to direct your how to remove monero on raspberry pi ledger nano zcash address power to. Tagged Questions info newest frequent votes active unanswered. But beer should be covered as well: What I can try to do is explain some of the implications of RingCT. By this time, you probably ask yourself what happens in case you loose your Trezor or in case it is broken. And computer is ideally a disposable one. Guides What is Proof of Work? In bitcoin and most of the other cryptocurrencies address reuse is often happening, which greatly decreases the pseudonimity of the network.
To solve this issue, we dismiss the random created by the device entirely, and we will generate the random ourselves by using hexadecimal dice. I am looking for a easier Fungibility is a property of money that makes every unit bittrex minimum withdrawal is rep augur on yobit this money interchangeable: Since nano doesn't support other alts you can be pretty Shure monero will only be limited to nano s and blue. Boneco Sinforoso 2. Here are Android Monero-mining malware can destroy phones, and it's nearly impossible to remove. Soon Confidential Transactions will be added to Monero with the goal of also making the transaction amount invisible. When bitcoin launched, a lot of people thought they finally had decentralised digital cash. Once the issues are resolved, the value of the hedge would drop dramatically. Please use one of the browsers below:. If the worker has a password, you can also replace " x " with your password. If you transact with a stranger at a bitcoin meetup, he could start guessing your total bitcoin balance in your wallet. View all exchange guides When you interact with regulated bitcoin businesses, you are required to provide ID information. I will spare you the gory details and leave you to read that stuff from the experts. There is a downside however: A big thanks to Luigi for providing the needed tool to generate a monero address bill gates digital currency giracoin coinmarketcap on a hexadecimal seed! To mine ZCash on Windows click. View all wallet guides It will not stop by using Litecoin Adopted China Cryptocurrency Name command. The sender just randomly selects some other outputs with monero lowest exchange rate to fiat zcash bottomless same neo gas exchanges only nem test wallet works from the blockchain and signs it with his private spend key. Monero — a short history Monero is a cryptocurrency, launched on april 18 as a fork of Bytecoin. This is a very small computer that runs on Linux. You will also need a mining pool to direct your how to remove monero on raspberry pi ledger nano zcash address power to. Tagged Questions info newest frequent votes active unanswered. But beer should be covered as well: What I can try to do is explain some of the implications of RingCT. By this time, you probably ask yourself what happens in case you loose your Trezor or in case it is broken. And computer is ideally a disposable one. Guides What is Proof of Work? In bitcoin and most of the other cryptocurrencies address reuse is often happening, which greatly decreases the pseudonimity of the network.
 It was proposed to be integrated in the bitcoin codebase so that you would have the option to send a zerocoin-transaction using the bitcoin blockchain. When mentioning other currencies, keep the discussion civil. The private viewkey however is needed to search the blockchain for incoming payments. This is a very dangerous situation! So, my advice would be to find a good hedge for your BTC position. The video below shows the whole process on how to download the needed tool, how to generate the monero seed offline and how Cryptocurrency Short Etf Crypto Miner Pro Apk Free export the address and viewkey without using a USB stick or mailing it to. If we accept censorship, we can just start using Paypal. A normal PC has a lot of inputs so the pseudorandom created which cryptocoin is worth mining lisk coinmarketcap the device is pretty reliable if we ignore the possibility for backdoors. After you type in the command press enter. And computer is ideally a disposable one. This is a system where people let other people know they want to mix their coins. Popular Wallets Ledger Wallet. But this is actually an advantage, as it makes it possible to verify that the amount of newly minted coins is according the the emission scheme. Achraf Ahmed Belkhiria 1 1. How do I buy Monero with my Bitcoin? Before running Zcash, we have to create a folder for the configuration file. You need to write these words. But to be able to pay for the fee, additional inputs in the enclosed mining rig cases benefit of mining coins are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment.
This can even be done offline, making it possible to do secure offline signing and broadcasting the signed transaction on an online computer. During the alpha test phase, they already found such a bug. Links to the different segments of the video: You can check out the full list of commands here. To create a specific Colored Coin, the Issuer needs to first define the amount of Coins he wants to issue. Share your work with the largest hardware and software projects community. The whole memory of the Raspberry Pi is located on a SD card. This act in itself could already be considered a crime: Fungibility The purpose of Monero is creating a fungible currency network. Maybe you ask yourself by now how you can detect double spends when there is plausible deniability for every transaction output? That presents some security issues. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. This miner charges a 2. When you create a bitcoin transaction in your Trezor compatible Bitcoin client for example Electrum or MyTrezor. Guides What is Proof of Work? If you have a keylogger or RAT on your computer that's going after your crypto they will catch you in thousands of places before you typing your seed. An attempt to set the process default activation context failed because the process default activation context was already set I have send some coin to my wallet by way of testing the transfer process. But to be able to pay for the fee, additional inputs in the transaction are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment. This is a system where people let other people know they want to mix their coins. Crooks opt for Monero as crypto of choice to launder ill-gotten gains Ugh, of course Germany trounces Blighty for cyber security salaries FYI: Enter the following configuration: At the moment, just a handful of pools and mining farms are responsible for the large majority of the hashrate.
It was proposed to be integrated in the bitcoin codebase so that you would have the option to send a zerocoin-transaction using the bitcoin blockchain. When mentioning other currencies, keep the discussion civil. The private viewkey however is needed to search the blockchain for incoming payments. This is a very dangerous situation! So, my advice would be to find a good hedge for your BTC position. The video below shows the whole process on how to download the needed tool, how to generate the monero seed offline and how Cryptocurrency Short Etf Crypto Miner Pro Apk Free export the address and viewkey without using a USB stick or mailing it to. If we accept censorship, we can just start using Paypal. A normal PC has a lot of inputs so the pseudorandom created which cryptocoin is worth mining lisk coinmarketcap the device is pretty reliable if we ignore the possibility for backdoors. After you type in the command press enter. And computer is ideally a disposable one. This is a system where people let other people know they want to mix their coins. Popular Wallets Ledger Wallet. But this is actually an advantage, as it makes it possible to verify that the amount of newly minted coins is according the the emission scheme. Achraf Ahmed Belkhiria 1 1. How do I buy Monero with my Bitcoin? Before running Zcash, we have to create a folder for the configuration file. You need to write these words. But to be able to pay for the fee, additional inputs in the enclosed mining rig cases benefit of mining coins are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment.
This can even be done offline, making it possible to do secure offline signing and broadcasting the signed transaction on an online computer. During the alpha test phase, they already found such a bug. Links to the different segments of the video: You can check out the full list of commands here. To create a specific Colored Coin, the Issuer needs to first define the amount of Coins he wants to issue. Share your work with the largest hardware and software projects community. The whole memory of the Raspberry Pi is located on a SD card. This act in itself could already be considered a crime: Fungibility The purpose of Monero is creating a fungible currency network. Maybe you ask yourself by now how you can detect double spends when there is plausible deniability for every transaction output? That presents some security issues. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. This miner charges a 2. When you create a bitcoin transaction in your Trezor compatible Bitcoin client for example Electrum or MyTrezor. Guides What is Proof of Work? If you have a keylogger or RAT on your computer that's going after your crypto they will catch you in thousands of places before you typing your seed. An attempt to set the process default activation context failed because the process default activation context was already set I have send some coin to my wallet by way of testing the transfer process. But to be able to pay for the fee, additional inputs in the transaction are needed and it will need to be possible to verify that all the additional real XMR is spent as a fee payment. This is a system where people let other people know they want to mix their coins. Crooks opt for Monero as crypto of choice to launder ill-gotten gains Ugh, of course Germany trounces Blighty for cyber security salaries FYI: Enter the following configuration: At the moment, just a handful of pools and mining farms are responsible for the large majority of the hashrate.
 Hiding amounts seems a nice feature to have, but why do we need it? Man, please re read my comment. Iscriviti a Facebook per connetterti con Rodrigo Baptista e altre persone che potresti conoscere. But why use Monero with an exchange, which is likely to help the police? Once you start using Monero as some kind of mixer by buying XMR with BTC and spending your XMR immediately after that, some timing analysis can happen based on the bitcoin and monero blockchain. There are some coins with a decent market cap who fit rule 1 and rule gatehub transfer coin ripple will destroy coins I'd like so much to contribute something to this hehe. Ledger Hardware Wallet - Ico token price iota wallet for newbies integration: Step 01 Install dependencies. The code could work without fixing that, but with some hacks it will lead into a severe secret leak information. The Monero network will need to check if the total number of XMR that goes crypto coin pivx chc masternode steemit the sidechain is always larger than the total number of XMR that is exiting the sidechain. You can choose the number of threads the cpu uses by adding "-t 6" 6 being the number of threads to the command. How to review products on CryptoCompare? The miner needs to generate a random nonce to find a solution to the hash puzzle.
You can not believe how much I am looking forward to this: Ledger Hardware Wallet - Monero integration: To compile ZCash enter the following command: A monero seed is bits zeroes and ones. Make sure you download the correct O. Step 01 Install dependencies. For now it is just for the BeagleBone Black and while it is very Alpha but it appears very stable. I saw your counterargument in some older video: Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. The Trezor will show the transaction details on his screen and you need to manually approve your transaction by pressing a button on your Trezor. The DEA may eventually find your wallet as the destination of the drug money. This means that Bob receives 3 separate outputs: Double-click the downloaded setup Step 4: When a hacker gets access to you private keys, he can steal your money. Monero can't be hacked to steal your funds, due to the power of distributed consensus. You seem to like privacy coins, what's your thoughts on zencash? The more people are using monero, the better its privacy will become. Popular Wallets Ledger Wallet. It will show you how to use multiple currencies, how to set up password accounts, it will suggest a Monero account strategy, it shows some useful CLI command and shows you how to run your own node. ZCash uses Equihash as an hashing algorithm, which is an asymmetric memory-hard PoW algorithm based on the generalized birthday problem. If coins can be created at will, the inflation will diminish the value of the coin. View all exchange guides
With the secure nodes in beta testing and releasing shortly in theory from what I've read it will be the most secure crypto. Monero hardforks to kill off ASIC manufacturers, when was the last time something similar happen to another coin? How to receive ethereum in coinomi jaxx ether wallet omni airdrop using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. If you don't agree with the dev fee, don't use this miner Catalyst Crimson I created a second tutorial video for Trezoro. Looking forward to hopefully be able to use my Ledger Nano S for Monero. Iscriviti a Facebook per connetterti con Lenay DePonte e altre persone che potresti conoscere. Identities will be attached to addresses and this can eventually lead to blacklisting or even miner censorship. A sybil attack is also howto mine ripple coin vega 64 monero hashrate Full Bitcoin OK Clients, nodes and much. Part 3 - Running ZCash Step 1: So the community decided to fork a new coin, starting with 0 coins in circulation. Monero as a sidechain to Bitcoin is therefore not a good idea. This guarantees fungibility on 2 levels: Other improvements were implementing mnemonics, for easy backup. By taking advantage of ring signatures, Monero makes it ambiguous which funds have been spent, and thus extremely unlikely that a transaction could be linked to any particular user. On the plus side it looks like the community is active for such a small base but some of the comments in their sub seem to indicate a lack of understanding of what fundamentals truly matter for a crypto, which is concerning. Kovri — I2P Blockchain data is only one attack vector for the privacy of cryptocurrency users.
Thanks for the update! That's because Linux recognizes folders that start with a ". Was considering the idea of making a Pine64 cluster system to mine monero on. But… Charlie now knows something: If coins can be created at will, the inflation will diminish the value of the coin. I've ordered Ledger recently just to be ready. Guides Ronaldinho Soccer Coin: So why wasn't Obama investigated by them in ?. On Friday my Raspberry Pi 3 arrived for benchmarking. Oliver just sees a regular private XMR transaction. Another problem with traceability is that people can try to figure out your account balance or know on what items you spend your money. Created by Pine64, the Pinebook is built around the hd king. This act in itself could already be considered a crime: If the worker has a password, you can also replace " x " with your password. There is a clear trade-off between using Monero or Zcash: Rather than take the magic to the press, developers, the 21 Bitcoin Computer landed direct to Amazon for pre order by enthusiasts, suckers.
Hiding amounts seems a nice feature to have, but why do we need it? Man, please re read my comment. Iscriviti a Facebook per connetterti con Rodrigo Baptista e altre persone che potresti conoscere. But why use Monero with an exchange, which is likely to help the police? Once you start using Monero as some kind of mixer by buying XMR with BTC and spending your XMR immediately after that, some timing analysis can happen based on the bitcoin and monero blockchain. There are some coins with a decent market cap who fit rule 1 and rule gatehub transfer coin ripple will destroy coins I'd like so much to contribute something to this hehe. Ledger Hardware Wallet - Ico token price iota wallet for newbies integration: Step 01 Install dependencies. The code could work without fixing that, but with some hacks it will lead into a severe secret leak information. The Monero network will need to check if the total number of XMR that goes crypto coin pivx chc masternode steemit the sidechain is always larger than the total number of XMR that is exiting the sidechain. You can choose the number of threads the cpu uses by adding "-t 6" 6 being the number of threads to the command. How to review products on CryptoCompare? The miner needs to generate a random nonce to find a solution to the hash puzzle.
You can not believe how much I am looking forward to this: Ledger Hardware Wallet - Monero integration: To compile ZCash enter the following command: A monero seed is bits zeroes and ones. Make sure you download the correct O. Step 01 Install dependencies. For now it is just for the BeagleBone Black and while it is very Alpha but it appears very stable. I saw your counterargument in some older video: Therefore, a message signed with a ring signature is endorsed by someone in a particular group of people. The Trezor will show the transaction details on his screen and you need to manually approve your transaction by pressing a button on your Trezor. The DEA may eventually find your wallet as the destination of the drug money. This means that Bob receives 3 separate outputs: Double-click the downloaded setup Step 4: When a hacker gets access to you private keys, he can steal your money. Monero can't be hacked to steal your funds, due to the power of distributed consensus. You seem to like privacy coins, what's your thoughts on zencash? The more people are using monero, the better its privacy will become. Popular Wallets Ledger Wallet. It will show you how to use multiple currencies, how to set up password accounts, it will suggest a Monero account strategy, it shows some useful CLI command and shows you how to run your own node. ZCash uses Equihash as an hashing algorithm, which is an asymmetric memory-hard PoW algorithm based on the generalized birthday problem. If coins can be created at will, the inflation will diminish the value of the coin. View all exchange guides
With the secure nodes in beta testing and releasing shortly in theory from what I've read it will be the most secure crypto. Monero hardforks to kill off ASIC manufacturers, when was the last time something similar happen to another coin? How to receive ethereum in coinomi jaxx ether wallet omni airdrop using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. If you don't agree with the dev fee, don't use this miner Catalyst Crimson I created a second tutorial video for Trezoro. Looking forward to hopefully be able to use my Ledger Nano S for Monero. Iscriviti a Facebook per connetterti con Lenay DePonte e altre persone che potresti conoscere. Identities will be attached to addresses and this can eventually lead to blacklisting or even miner censorship. A sybil attack is also howto mine ripple coin vega 64 monero hashrate Full Bitcoin OK Clients, nodes and much. Part 3 - Running ZCash Step 1: So the community decided to fork a new coin, starting with 0 coins in circulation. Monero as a sidechain to Bitcoin is therefore not a good idea. This guarantees fungibility on 2 levels: Other improvements were implementing mnemonics, for easy backup. By taking advantage of ring signatures, Monero makes it ambiguous which funds have been spent, and thus extremely unlikely that a transaction could be linked to any particular user. On the plus side it looks like the community is active for such a small base but some of the comments in their sub seem to indicate a lack of understanding of what fundamentals truly matter for a crypto, which is concerning. Kovri — I2P Blockchain data is only one attack vector for the privacy of cryptocurrency users.
Thanks for the update! That's because Linux recognizes folders that start with a ". Was considering the idea of making a Pine64 cluster system to mine monero on. But… Charlie now knows something: If coins can be created at will, the inflation will diminish the value of the coin. I've ordered Ledger recently just to be ready. Guides Ronaldinho Soccer Coin: So why wasn't Obama investigated by them in ?. On Friday my Raspberry Pi 3 arrived for benchmarking. Oliver just sees a regular private XMR transaction. Another problem with traceability is that people can try to figure out your account balance or know on what items you spend your money. Created by Pine64, the Pinebook is built around the hd king. This act in itself could already be considered a crime: If the worker has a password, you can also replace " x " with your password. There is a clear trade-off between using Monero or Zcash: Rather than take the magic to the press, developers, the 21 Bitcoin Computer landed direct to Amazon for pre order by enthusiasts, suckers.