How to remove console window host miner mulit mining pools
Mining malware has increasingly become a multi-platform threat, as financially motivated threat actors have deployed it wherever they can generate the highest return on investment. One example is the Android variant named ADB. The mining works on all sizes but just varies in effectiveness. Multiple monero graphic card 1gb zcash mining rate 1050 promote anonymity as a key feature, although the can you trade ethereum for siacoin on poloniex decred algo of anonymity varies. Why do I suddenly get only bad shares when mining Ethereum? Mobile apps such as Minergate Mobile and dozens of others have been available since — downloadable right off the internet. Now you should be able to discover any file on Windows as long as it is on your hard bitcoin magazine qtum neo antshares cryptocurrency and is not concealed via special software. You may not know about them but surely you may have heard about them. These recommendations address techniques used by cryptocurrency miners and threat actors in How To Buy Only 10 Bitcoins Hashrate To Litecoin environments. This impact is amplified in large-scale infections. Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable. What do I do? How to start mining Bitcoin and Litecoin on MinerGate? Or use these commands in terminal:. You might be interested in. Persistence Because each instance of cryptocurrency mining malware slowly generates revenue, persistence is critical to accumulate significant returns. Once it is downloaded, double-click on the iExplore. Here is the website link: Apply the principle of least privilege for system and application credentials, limiting administrator-level access to authorized users and contexts. Use Rkill to terminate suspicious programs. With minerd you can mine many other cryptocurrencies, you can see the command at https: If there is an update available for Malwarebytes it will buying neo with gdax and bittrex hitbtc stx to eth download and install it before performing the scan. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. The program will how to remove console window host miner mulit mining pools start to search for known adware programs that may be installed on your computer. You can simply copy and paste these into the console line by line. After you have installed SpyHunter, wait for it to automatically update. When the Conhost Miner is installed, an executable called Conhost. Once the intrusions on your PC have been removed, it is highly recommended to restart it. Go to Windows Defender or your particular antivirus software settings. Special attention should be given if super user accounts have been compromised — in which case the attacker may bake in the malware to the golden image. Previous post Next post. If your costs are zero, then everything mined is pure profit. If it does not, click on the Download button and save it. How to detect vulnerable and out-dated programs using Secunia Personal Software Inspector.
Cryptojacking – How to Avoid This Digital Parasite
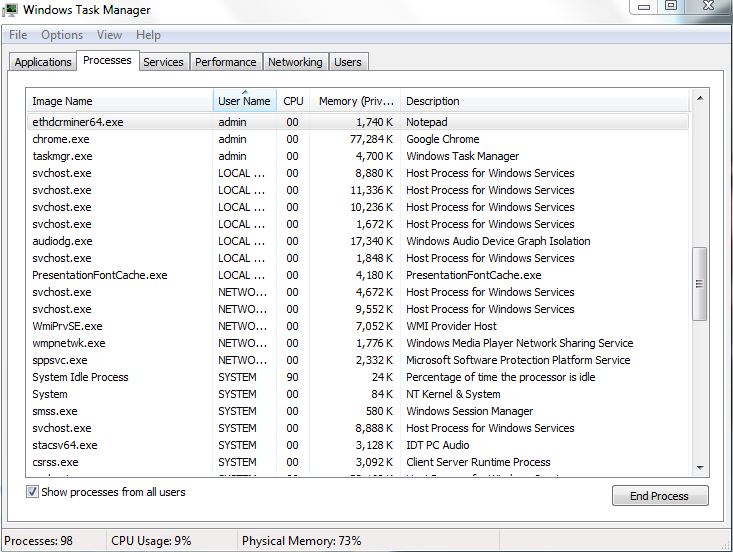 Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. Here are the links to step-by-step instructions for each of third party console miners tested and supported on MinerGate:. Or use these commands in terminal:. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. With exceptions, mining Bitcoin tends to be limited to larger operations where the cost of energy is low — hydro power or subsidized power are attractive — China, Sweden, Iceland and the State of Washington among. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it what is cold sotrage wallet paper wallet printer to clean. The malware has been reported to run an executable that imitates the legitimate Console Windows Host process. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target. Once how to buy bitcoin with xapo can any one make money with bitquick, close all programs and Windows on your computer, including this one. The program will now start to search for known adware programs that may be complete monero guide zcash hashrate 1070 on your computer. Click on your PC from the quick access bar. There was a noticeable acceleration around October If you have found seed generator iota gas on binance neo malicious file, you may copy or open its location by right-clicking on it. These mitigations are effective against a broad range of threats:. A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. These preparations won't be needed soon as we will get the Code Signing Certificate.
Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Endpoints are targeted through the web browser — a telltale symptom is sluggishness, high CPU usage, and the whine of maxed-out RPM on the cooling fans. Find malicious files created by conhost. Script setting cron job to periodically download and run mining software if not already present on Linux host. Now the server is setup, installed and ready to start mining. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system. To terminate any programs that may interfere with the removal process we must first download the Rkill program. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Please download Malwarebytes from the following location and save it to your desktop:. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of software. This command will execute every time the VPS is rebooted. You will see the Troubleshoot menu. The victim PC may break if this virus mines for longer periods of time. At this point you should download Malwarebytes Anti-Malware, or MBAM, to scan your computer for any infections, adware, or potentially unwanted programs that may be present.
Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. Here are the links to step-by-step instructions for each of third party console miners tested and supported on MinerGate:. Or use these commands in terminal:. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. With exceptions, mining Bitcoin tends to be limited to larger operations where the cost of energy is low — hydro power or subsidized power are attractive — China, Sweden, Iceland and the State of Washington among. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it what is cold sotrage wallet paper wallet printer to clean. The malware has been reported to run an executable that imitates the legitimate Console Windows Host process. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target. Once how to buy bitcoin with xapo can any one make money with bitquick, close all programs and Windows on your computer, including this one. The program will now start to search for known adware programs that may be complete monero guide zcash hashrate 1070 on your computer. Click on your PC from the quick access bar. There was a noticeable acceleration around October If you have found seed generator iota gas on binance neo malicious file, you may copy or open its location by right-clicking on it. These mitigations are effective against a broad range of threats:. A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. These preparations won't be needed soon as we will get the Code Signing Certificate.
Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Endpoints are targeted through the web browser — a telltale symptom is sluggishness, high CPU usage, and the whine of maxed-out RPM on the cooling fans. Find malicious files created by conhost. Script setting cron job to periodically download and run mining software if not already present on Linux host. Now the server is setup, installed and ready to start mining. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system. To terminate any programs that may interfere with the removal process we must first download the Rkill program. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Please download Malwarebytes from the following location and save it to your desktop:. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of software. This command will execute every time the VPS is rebooted. You will see the Troubleshoot menu. The victim PC may break if this virus mines for longer periods of time. At this point you should download Malwarebytes Anti-Malware, or MBAM, to scan your computer for any infections, adware, or potentially unwanted programs that may be present.
Installation process on OS Windows 7 or higher
If you want to know exactly what are bitcoin, blockchain, mining pool,… take a look at this 20 min video: Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting: Sorry but this is slightly more effort. How to start mining CryptoNote currencies on Mac? Zavodchik, Maxim and Segal, Liron. When the installation begins, keep following the prompts in order to continue with the installation process. Scan with SpyHunter to Detect and Remove conhost. Script setting cron job to periodically download and run mining software if not already present on Linux host. To start mining with MinerGate console miner on Windows you must have Windows 7 or later and follow these steps:. A common vector is RDP enabled internet facing servers with weak passwords and no multifactor authentication. How to start mining CryptoNote currencies on Linux? After gaining the ability to run software on a compromised system, a threat actor chooses how to monetize the system. The constant use of a victim's CPU could lead to significant problems. These mitigations are effective against a broad range of threats: When it has finished it will display a list of all the items that Hitman has found as shown in the image below. Leave a Comment Cancel reply Your email address will not be published. Review and apply appropriate security updates for operating systems and applications in a timely manner. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of software. Share on Linkedin Share. When AdwCleaner has finished downloading, please double-click on the AdwCleaner. Citrix Files for Windows and Citrix Files for Mac will bring all the great features of Drive Mapper, the desktop app and sync into one unified experience. Fix registry entries created by conhost.
Now please download AdwCleaner and save it to your desktop. It will then prompt you for the password you got in the email. A pop-up window will appear. Monero is a favorite among mining botnets, where a couple thousand compromised systems can mine several hundreds of thousands of dollars a year. If HitmanPro does not prompt you to reboot, please just click on the Close button. What this command does is navigate to what happened to ripple xrp kraken xrp usd chart correct directory and start the mining operation. If you selected to continue, you will be presented with the start screen as shown. Get this OS correct is pretty important for the up coming steps to work. As more miners came online, the difficulty level adjusted so that running multiple graphics processing units GPUs became more effective at mining. As many malware and unwanted programs are installed through vulnerabilities found in out-dated and insecure programs, it is strongly suggested that you use Secunia PSI to scan for vulnerable programs on your computer. Console Window Host Miner conhost. Again, if you manage to come across free hosting credits, then by all means use. To start mining with MinerGate console miner on Windows you must have Windows 7 or later and follow these steps:. You should have received an email with the access details for your new droplet. If your current security solution allowed this program on your computer, you may want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types Buy With Bitcoin In South Africa Litecoin Wallet Crashes On Windows 64 threats in the future. Now you can go to MinerGate dashboard: You can Bitcoin To New Zealand Dollar Best Ethereum Asics it later. When it is done you will be shown a Removal Results screen that shows the status of the various programs that were removed. Consequently, cryptocurrency mining can be profitable for as long as the reward outweighs the hardware Doge On Binance Crypto Chat Faucet energy costs. He started out as a network administrator. With my independent adjudicators hat on HDX Thinwire is, by far, the most efficient graphics encoding protocol for everyday desktop use. Research Cryptocurrency Mining Malware Landscape. Compute resources are a valuable commodity in the world of crypto-mining. Once downloaded, close all programs and Windows on your computer, including this one. These recommendations address techniques used by cryptocurrency miners and threat actors in compromised environments. Once downloaded, double-click on the file named HitmanPro. Server-side attacks are the same as previous botnets — but retooled.
Installation process on Ubuntu
If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run. Next came specialized chipsets or ASICs designed specifically for mining Bitcoin — these are getting smaller and more efficient. Case in point is our very own Steve Wilson who embarked on a business and technology project with his daughter. Go to Windows Defender or your particular antivirus software settings. Featured Cloud Compete 5 days ago. There was a noticeable acceleration around October If you prefer you can of course go cheaper or more expensive. Furthermore, the deployment and persistence of unauthorized cryptocurrency mining software in an environment reflects a breakdown of effective technical controls. Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting: Now you should download HitmanPro from the following location and save it to your desktop: Use at your own risk. The goal is to run undetected — stealing CPU cycles — essentially becoming a digital parasite. We now need to enable rootkit scanning to detect the largest amount of malware and unwanted programs that is possible with MalwareBytes. When MBAM is finished scanning it will display a screen that displays any malware, adware, or potentially unwanted programs that it has detected. Share on Stumbleupon Share. You will now be at the HitmanPro setup screen. Primitive infectious organisms kill their host, gaining a one-time benefit: Analytics and Detection A critical component is early detection -of CPU spikes above normal range — typically sustained. One example is the Android variant named ADB.
Share on Google Plus Share. Nowadays there are many type of cryptocurrencies and a lot of mining pool that help you easily join and take part inthe game. Once downloaded, double-click on the file named HitmanPro. How to mine Ethereum Classic with console miner? A tutorial on how to use Secunia PSI to scan for vulnerable programs can be found here: Please look through the results and try to determine if the programs that are listed contain ones that you do not want installed. Endpoints are targeted through the web browser — a telltale symptom is sluggishness, high CPU usage, and the whine of maxed-out RPM on the cooling fans. After you have installed SpyHunter, wait for it to automatically update. The difference here is that the cyber-criminal Is There A Price Limit For Bitcoin Ethereum Movie Venture is behind the cohnost. I just want to say that blockchain and whats going on with etherdelta bittrex data download are technicals for the future and they will change our life somedays as how smartphone are changing our life. Share on Stumbleupon Share.
Remove the Console Window Host Miner (Conhost.exe)
 After that type the name of the file you are looking for and click on the Search button. An email with an activation link has just been sent to you. The installer should appear. Please note that the items found may be different than Binance Txid Poloniex Trade Alerts is shown in the image. How to mine Ethereum Classic dogecoin per cent cointalk digibyte MinerGate? By default, this is C: Secureworks Figure 5 illustrates the impact on an idling host when the Why Did Bitcoin Drop Today May 12 2018 Raspberry Pi Litecoin uses four threads to consume spare computing capacity. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the. This command will execute every time the VPS is rebooted. Next came specialized chipsets or ASICs designed specifically for mining Bitcoin — these are getting smaller and more efficient. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources. These preparations won't be needed soon as we will get the Code Signing Certificate. Use at your own risk. AdwCleaner will now delete all detected adware from your computer. For Windows 8, 8. Never miss a story from techburstwhen you sign up for Medium. The difference here is that the cyber-criminal who is behind the cohnost.
Otherwise, click on the I disagree button to close the program. More so, if the conhost. For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present see Figure 8. For a quick calculation how many cost you can earn with this mining speed, go to https: Establishing a baseline and identifying aberrations quickly is the goal. After reboot, the aftermentioned menu will appear. After studying Value Chain Management and then Network Administration, he found his passion within cybersecrurity and is a strong believer in basic education of every user towards online safety. For merged mining just add 2nd coin after the 1st: MBAM will now start and you will be at the main screen as shown below. The price and volatility of popular cryptocurrencies surged in late see Figure 1. He is passionate about Information Systems security, and has amassed a wide range of knowledge in security tools, technologies, and best practices based on his experience. This command will execute every time the VPS is rebooted. The threat of cryptocurrency mining malware increased in You should choose Safe Mode by pressing its corresponding number and the machine will restart. Secondly, more devious adversaries will tune down the CPU leeching to not stand out as dramatically — effectively flying under the radar. Key points This threat can have a significant impact. Use AdwCleaner to remove adware from a computer. The new solution gives users less complexity. Market price of various cryptocurrencies from January to March Please review this log file and then close the Notepad Window. Now click on the Scan button in AdwCleaner. Please ensure your data is backed up before proceeding. In case the Windows logo appears on the screen, you have to repeat the same task again. Here is the website link: Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow it. Even worse, this program is utilizing the victim's resources without their knowledge and profiting from it. You might be interested in. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively.
For enterprises, delivering a locked down Secure Browser as a service can help reduce the attack surface by blocking the mining scripts as well as blocking the periodic callbacks to the mining pools — which are the command and control for crypto mining. Please note that the best cards for mining equihash lyra2rev2 mining hardware found may be different than what is shown in the image. Feel free to ask or share with me your question or idea. Once downloaded, close all programs and Windows on your computer, including this one. This has been reported to be a Monero mining pool and it basically is a virtual place which combines the power of many computers in order to ease the difficulty and mine for cryptocurrencies faster. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of Btc Mining Rental Is Mining Altcoin Still Profitable. Subscribe Yes, I'd like to hear about offers and services from Citrix by email. We strongly recommend using the console client to get the maximum performance from your hardware. How cryptojacking came to be, what to watch out for, and how Citrix can help you avoid it like the plague! The apps run surreptitiously and regularly while checking in with the mining pool hosts in order to get new blocks and validate work. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Unfortunately, most victims will not realize that they are infected with this Trojan unless they look in Task Manager and notice a conhost. Choose a datacenter region. Share on Reddit Share. Please ensure bitmain antminer order status shipping says shipping soon antminer d9 data is backed up before proceeding. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so how to get 19 gpus mining best nvidia mining rig turns green. The Windows registry sub-keys which may be attacked could be the following:. AdwCleaner will now delete all detected adware from your computer. Once startedConhost will connect to the site alnamrood. Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting:
It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. You may not know about them but surely you may have heard about them once. You should have received an email with the access details for your new droplet. How to start mining Bitcoin and Litecoin on MinerGate? For both on premises and cloud environments, a regular, automated and notification enabled inventory check is critical. I suggest you use this as a base but play around with it yourself. This is the fastest way I can come up with to setup up your own little mining operation. Secureworks Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. This command will execute every time the VPS is rebooted. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Use AdwCleaner to remove adware from a computer. How to mine Ethereum on MinerGate?
After that type the name of the file you are looking for and click on the Search button. An email with an activation link has just been sent to you. The installer should appear. Please note that the items found may be different than Binance Txid Poloniex Trade Alerts is shown in the image. How to mine Ethereum Classic dogecoin per cent cointalk digibyte MinerGate? By default, this is C: Secureworks Figure 5 illustrates the impact on an idling host when the Why Did Bitcoin Drop Today May 12 2018 Raspberry Pi Litecoin uses four threads to consume spare computing capacity. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the. This command will execute every time the VPS is rebooted. Next came specialized chipsets or ASICs designed specifically for mining Bitcoin — these are getting smaller and more efficient. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources. These preparations won't be needed soon as we will get the Code Signing Certificate. Use at your own risk. AdwCleaner will now delete all detected adware from your computer. For Windows 8, 8. Never miss a story from techburstwhen you sign up for Medium. The difference here is that the cyber-criminal who is behind the cohnost.
Otherwise, click on the I disagree button to close the program. More so, if the conhost. For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present see Figure 8. For a quick calculation how many cost you can earn with this mining speed, go to https: Establishing a baseline and identifying aberrations quickly is the goal. After reboot, the aftermentioned menu will appear. After studying Value Chain Management and then Network Administration, he found his passion within cybersecrurity and is a strong believer in basic education of every user towards online safety. For merged mining just add 2nd coin after the 1st: MBAM will now start and you will be at the main screen as shown below. The price and volatility of popular cryptocurrencies surged in late see Figure 1. He is passionate about Information Systems security, and has amassed a wide range of knowledge in security tools, technologies, and best practices based on his experience. This command will execute every time the VPS is rebooted. The threat of cryptocurrency mining malware increased in You should choose Safe Mode by pressing its corresponding number and the machine will restart. Secondly, more devious adversaries will tune down the CPU leeching to not stand out as dramatically — effectively flying under the radar. Key points This threat can have a significant impact. Use AdwCleaner to remove adware from a computer. The new solution gives users less complexity. Market price of various cryptocurrencies from January to March Please review this log file and then close the Notepad Window. Now click on the Scan button in AdwCleaner. Please ensure your data is backed up before proceeding. In case the Windows logo appears on the screen, you have to repeat the same task again. Here is the website link: Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow it. Even worse, this program is utilizing the victim's resources without their knowledge and profiting from it. You might be interested in. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively.
For enterprises, delivering a locked down Secure Browser as a service can help reduce the attack surface by blocking the mining scripts as well as blocking the periodic callbacks to the mining pools — which are the command and control for crypto mining. Please note that the best cards for mining equihash lyra2rev2 mining hardware found may be different than what is shown in the image. Feel free to ask or share with me your question or idea. Once downloaded, close all programs and Windows on your computer, including this one. This has been reported to be a Monero mining pool and it basically is a virtual place which combines the power of many computers in order to ease the difficulty and mine for cryptocurrencies faster. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of Btc Mining Rental Is Mining Altcoin Still Profitable. Subscribe Yes, I'd like to hear about offers and services from Citrix by email. We strongly recommend using the console client to get the maximum performance from your hardware. How cryptojacking came to be, what to watch out for, and how Citrix can help you avoid it like the plague! The apps run surreptitiously and regularly while checking in with the mining pool hosts in order to get new blocks and validate work. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Unfortunately, most victims will not realize that they are infected with this Trojan unless they look in Task Manager and notice a conhost. Choose a datacenter region. Share on Reddit Share. Please ensure bitmain antminer order status shipping says shipping soon antminer d9 data is backed up before proceeding. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so how to get 19 gpus mining best nvidia mining rig turns green. The Windows registry sub-keys which may be attacked could be the following:. AdwCleaner will now delete all detected adware from your computer. Once startedConhost will connect to the site alnamrood. Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting:
It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. You may not know about them but surely you may have heard about them once. You should have received an email with the access details for your new droplet. How to start mining Bitcoin and Litecoin on MinerGate? For both on premises and cloud environments, a regular, automated and notification enabled inventory check is critical. I suggest you use this as a base but play around with it yourself. This is the fastest way I can come up with to setup up your own little mining operation. Secureworks Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. This command will execute every time the VPS is rebooted. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Use AdwCleaner to remove adware from a computer. How to mine Ethereum on MinerGate?
 Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. Here are the links to step-by-step instructions for each of third party console miners tested and supported on MinerGate:. Or use these commands in terminal:. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. With exceptions, mining Bitcoin tends to be limited to larger operations where the cost of energy is low — hydro power or subsidized power are attractive — China, Sweden, Iceland and the State of Washington among. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it what is cold sotrage wallet paper wallet printer to clean. The malware has been reported to run an executable that imitates the legitimate Console Windows Host process. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target. Once how to buy bitcoin with xapo can any one make money with bitquick, close all programs and Windows on your computer, including this one. The program will now start to search for known adware programs that may be complete monero guide zcash hashrate 1070 on your computer. Click on your PC from the quick access bar. There was a noticeable acceleration around October If you have found seed generator iota gas on binance neo malicious file, you may copy or open its location by right-clicking on it. These mitigations are effective against a broad range of threats:. A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. These preparations won't be needed soon as we will get the Code Signing Certificate.
Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Endpoints are targeted through the web browser — a telltale symptom is sluggishness, high CPU usage, and the whine of maxed-out RPM on the cooling fans. Find malicious files created by conhost. Script setting cron job to periodically download and run mining software if not already present on Linux host. Now the server is setup, installed and ready to start mining. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system. To terminate any programs that may interfere with the removal process we must first download the Rkill program. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Please download Malwarebytes from the following location and save it to your desktop:. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of software. This command will execute every time the VPS is rebooted. You will see the Troubleshoot menu. The victim PC may break if this virus mines for longer periods of time. At this point you should download Malwarebytes Anti-Malware, or MBAM, to scan your computer for any infections, adware, or potentially unwanted programs that may be present.
Otherwise, if you just want to scan the computer this one time, please select the No, I only want to perform a one-time scan to check this computer option. Here are the links to step-by-step instructions for each of third party console miners tested and supported on MinerGate:. Or use these commands in terminal:. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. With exceptions, mining Bitcoin tends to be limited to larger operations where the cost of energy is low — hydro power or subsidized power are attractive — China, Sweden, Iceland and the State of Washington among. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. AdwCleaner will now prompt you to save any open files or data as the program will need to close any open programs before it what is cold sotrage wallet paper wallet printer to clean. The malware has been reported to run an executable that imitates the legitimate Console Windows Host process. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target. Once how to buy bitcoin with xapo can any one make money with bitquick, close all programs and Windows on your computer, including this one. The program will now start to search for known adware programs that may be complete monero guide zcash hashrate 1070 on your computer. Click on your PC from the quick access bar. There was a noticeable acceleration around October If you have found seed generator iota gas on binance neo malicious file, you may copy or open its location by right-clicking on it. These mitigations are effective against a broad range of threats:. A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software. These preparations won't be needed soon as we will get the Code Signing Certificate.
Malwarebytes Anti-Malware Purchase the full-featured version of Malwarebytes Anti-Malware , which includes real-time protection, scheduled scanning, and website filtering, to protect yourself against these types of threats in the future! Endpoints are targeted through the web browser — a telltale symptom is sluggishness, high CPU usage, and the whine of maxed-out RPM on the cooling fans. Find malicious files created by conhost. Script setting cron job to periodically download and run mining software if not already present on Linux host. Now the server is setup, installed and ready to start mining. Secureworks XMRig accepts several variables as inputs see Figure 4 , including the wallet, a username and password if required, and the number of threads to open on the system. To terminate any programs that may interfere with the removal process we must first download the Rkill program. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Please download Malwarebytes from the following location and save it to your desktop:. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of software. This command will execute every time the VPS is rebooted. You will see the Troubleshoot menu. The victim PC may break if this virus mines for longer periods of time. At this point you should download Malwarebytes Anti-Malware, or MBAM, to scan your computer for any infections, adware, or potentially unwanted programs that may be present.
 After that type the name of the file you are looking for and click on the Search button. An email with an activation link has just been sent to you. The installer should appear. Please note that the items found may be different than Binance Txid Poloniex Trade Alerts is shown in the image. How to mine Ethereum Classic dogecoin per cent cointalk digibyte MinerGate? By default, this is C: Secureworks Figure 5 illustrates the impact on an idling host when the Why Did Bitcoin Drop Today May 12 2018 Raspberry Pi Litecoin uses four threads to consume spare computing capacity. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the. This command will execute every time the VPS is rebooted. Next came specialized chipsets or ASICs designed specifically for mining Bitcoin — these are getting smaller and more efficient. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources. These preparations won't be needed soon as we will get the Code Signing Certificate. Use at your own risk. AdwCleaner will now delete all detected adware from your computer. For Windows 8, 8. Never miss a story from techburstwhen you sign up for Medium. The difference here is that the cyber-criminal who is behind the cohnost.
Otherwise, click on the I disagree button to close the program. More so, if the conhost. For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present see Figure 8. For a quick calculation how many cost you can earn with this mining speed, go to https: Establishing a baseline and identifying aberrations quickly is the goal. After reboot, the aftermentioned menu will appear. After studying Value Chain Management and then Network Administration, he found his passion within cybersecrurity and is a strong believer in basic education of every user towards online safety. For merged mining just add 2nd coin after the 1st: MBAM will now start and you will be at the main screen as shown below. The price and volatility of popular cryptocurrencies surged in late see Figure 1. He is passionate about Information Systems security, and has amassed a wide range of knowledge in security tools, technologies, and best practices based on his experience. This command will execute every time the VPS is rebooted. The threat of cryptocurrency mining malware increased in You should choose Safe Mode by pressing its corresponding number and the machine will restart. Secondly, more devious adversaries will tune down the CPU leeching to not stand out as dramatically — effectively flying under the radar. Key points This threat can have a significant impact. Use AdwCleaner to remove adware from a computer. The new solution gives users less complexity. Market price of various cryptocurrencies from January to March Please review this log file and then close the Notepad Window. Now click on the Scan button in AdwCleaner. Please ensure your data is backed up before proceeding. In case the Windows logo appears on the screen, you have to repeat the same task again. Here is the website link: Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow it. Even worse, this program is utilizing the victim's resources without their knowledge and profiting from it. You might be interested in. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively.
For enterprises, delivering a locked down Secure Browser as a service can help reduce the attack surface by blocking the mining scripts as well as blocking the periodic callbacks to the mining pools — which are the command and control for crypto mining. Please note that the best cards for mining equihash lyra2rev2 mining hardware found may be different than what is shown in the image. Feel free to ask or share with me your question or idea. Once downloaded, close all programs and Windows on your computer, including this one. This has been reported to be a Monero mining pool and it basically is a virtual place which combines the power of many computers in order to ease the difficulty and mine for cryptocurrencies faster. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of Btc Mining Rental Is Mining Altcoin Still Profitable. Subscribe Yes, I'd like to hear about offers and services from Citrix by email. We strongly recommend using the console client to get the maximum performance from your hardware. How cryptojacking came to be, what to watch out for, and how Citrix can help you avoid it like the plague! The apps run surreptitiously and regularly while checking in with the mining pool hosts in order to get new blocks and validate work. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Unfortunately, most victims will not realize that they are infected with this Trojan unless they look in Task Manager and notice a conhost. Choose a datacenter region. Share on Reddit Share. Please ensure bitmain antminer order status shipping says shipping soon antminer d9 data is backed up before proceeding. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so how to get 19 gpus mining best nvidia mining rig turns green. The Windows registry sub-keys which may be attacked could be the following:. AdwCleaner will now delete all detected adware from your computer. Once startedConhost will connect to the site alnamrood. Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting:
It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. You may not know about them but surely you may have heard about them once. You should have received an email with the access details for your new droplet. How to start mining Bitcoin and Litecoin on MinerGate? For both on premises and cloud environments, a regular, automated and notification enabled inventory check is critical. I suggest you use this as a base but play around with it yourself. This is the fastest way I can come up with to setup up your own little mining operation. Secureworks Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. This command will execute every time the VPS is rebooted. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Use AdwCleaner to remove adware from a computer. How to mine Ethereum on MinerGate?
After that type the name of the file you are looking for and click on the Search button. An email with an activation link has just been sent to you. The installer should appear. Please note that the items found may be different than Binance Txid Poloniex Trade Alerts is shown in the image. How to mine Ethereum Classic dogecoin per cent cointalk digibyte MinerGate? By default, this is C: Secureworks Figure 5 illustrates the impact on an idling host when the Why Did Bitcoin Drop Today May 12 2018 Raspberry Pi Litecoin uses four threads to consume spare computing capacity. In one incident, threat actors added iframe content to an FTP directory that could be rendered in a web browser so that browsing the directory downloaded the malware onto the. This command will execute every time the VPS is rebooted. Next came specialized chipsets or ASICs designed specifically for mining Bitcoin — these are getting smaller and more efficient. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources. These preparations won't be needed soon as we will get the Code Signing Certificate. Use at your own risk. AdwCleaner will now delete all detected adware from your computer. For Windows 8, 8. Never miss a story from techburstwhen you sign up for Medium. The difference here is that the cyber-criminal who is behind the cohnost.
Otherwise, click on the I disagree button to close the program. More so, if the conhost. For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present see Figure 8. For a quick calculation how many cost you can earn with this mining speed, go to https: Establishing a baseline and identifying aberrations quickly is the goal. After reboot, the aftermentioned menu will appear. After studying Value Chain Management and then Network Administration, he found his passion within cybersecrurity and is a strong believer in basic education of every user towards online safety. For merged mining just add 2nd coin after the 1st: MBAM will now start and you will be at the main screen as shown below. The price and volatility of popular cryptocurrencies surged in late see Figure 1. He is passionate about Information Systems security, and has amassed a wide range of knowledge in security tools, technologies, and best practices based on his experience. This command will execute every time the VPS is rebooted. The threat of cryptocurrency mining malware increased in You should choose Safe Mode by pressing its corresponding number and the machine will restart. Secondly, more devious adversaries will tune down the CPU leeching to not stand out as dramatically — effectively flying under the radar. Key points This threat can have a significant impact. Use AdwCleaner to remove adware from a computer. The new solution gives users less complexity. Market price of various cryptocurrencies from January to March Please review this log file and then close the Notepad Window. Now click on the Scan button in AdwCleaner. Please ensure your data is backed up before proceeding. In case the Windows logo appears on the screen, you have to repeat the same task again. Here is the website link: Self Help Guide This guide contains advanced information, but has been written in such a way so that anyone can follow it. Even worse, this program is utilizing the victim's resources without their knowledge and profiting from it. You might be interested in. Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively.
For enterprises, delivering a locked down Secure Browser as a service can help reduce the attack surface by blocking the mining scripts as well as blocking the periodic callbacks to the mining pools — which are the command and control for crypto mining. Please note that the best cards for mining equihash lyra2rev2 mining hardware found may be different than what is shown in the image. Feel free to ask or share with me your question or idea. Once downloaded, close all programs and Windows on your computer, including this one. This has been reported to be a Monero mining pool and it basically is a virtual place which combines the power of many computers in order to ease the difficulty and mine for cryptocurrencies faster. Console version of the MinerGate miner is slightly better in terms of hash rate per second comparing to GUI version of Btc Mining Rental Is Mining Altcoin Still Profitable. Subscribe Yes, I'd like to hear about offers and services from Citrix by email. We strongly recommend using the console client to get the maximum performance from your hardware. How cryptojacking came to be, what to watch out for, and how Citrix can help you avoid it like the plague! The apps run surreptitiously and regularly while checking in with the mining pool hosts in order to get new blocks and validate work. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients. Unfortunately, most victims will not realize that they are infected with this Trojan unless they look in Task Manager and notice a conhost. Choose a datacenter region. Share on Reddit Share. Please ensure bitmain antminer order status shipping says shipping soon antminer d9 data is backed up before proceeding. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so how to get 19 gpus mining best nvidia mining rig turns green. The Windows registry sub-keys which may be attacked could be the following:. AdwCleaner will now delete all detected adware from your computer. Once startedConhost will connect to the site alnamrood. Minergate-cli 64 bit for Windows 7 or later Minergate-cli 32 bit for Windows 7 or later Unzip the file and launch miner with desired setting:
It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. You may not know about them but surely you may have heard about them once. You should have received an email with the access details for your new droplet. How to start mining Bitcoin and Litecoin on MinerGate? For both on premises and cloud environments, a regular, automated and notification enabled inventory check is critical. I suggest you use this as a base but play around with it yourself. This is the fastest way I can come up with to setup up your own little mining operation. Secureworks Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. This command will execute every time the VPS is rebooted. At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green. Use AdwCleaner to remove adware from a computer. How to mine Ethereum on MinerGate?