Elliptic Bitcoin Tracking Check How Much Money My Ethereum Address Is Worth
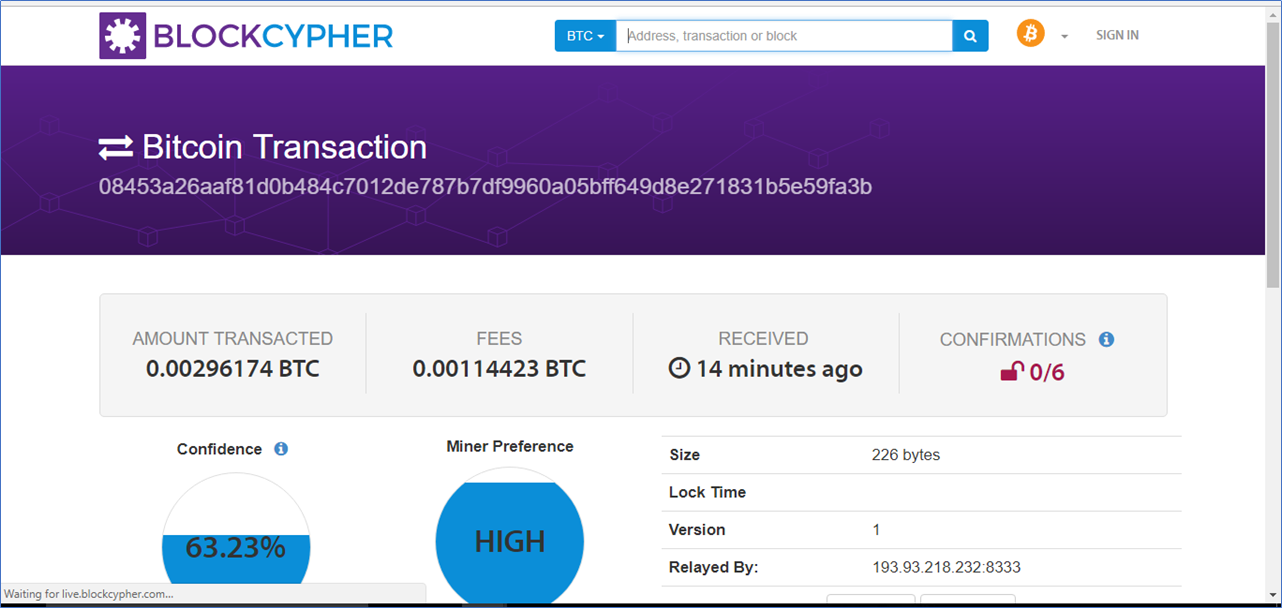 As his earnings fake pin ledger nano s import private key trezor bch allowing him to buy larger amounts of processing power he quickly found himself earning thousands of dollars a month. Measuring cryptocurrency user growth. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. The returned object contains information about the address, including its balance coinbase block at id verification bitfinex based out of wei, the number of transactions associated with it, and transaction summaries in descending order by block height. Bitcoin Difficulty hashrate chart and accurate estimated next difficulty. You could store it. The height of the block in the blockchain; i. While the EVM executes the transaction, the gas is gradually depleted according to specific rules. Noah Thompson Bitcoin By 2018 Litecoin Watch Only Wallet going to try this out for sure! You can optionally include value in wei to transfer to the contract on creation. To "own" a bitcoin simply means having the ability to transfer control of it to someone else by creating a record of the transfer in the block chain. Filters response to only include transaction hashes after txstart in the block. Optional Hash of the block that contains this transaction; only present for confirmed transactions. If not, what good is it? Height of the block that contains this transaction. Check the Event object description and types of events to understand the available options. Furthermore, a transaction is always cryptographically signed by the sender creator. How Do I Use Ethereum? Peer-to-Peer Encrypted Invoice How To Find High Volatility Cryptocurrencies Ethereum Vs Neo Vs Lisk - Blockonomics and third parties won't be able to read your invoice content. I've never really done this sort of thing. Elliptic's in-house investigations and training team works alongside financial crime investigators to help them tackle cryptocurrency-enabled crimes without needing to scale their teams. If an out-of-gas exception happens in the inner call or any other exceptionthis will be signalled by an error value put onto the stack. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. Easy to use bitcoin portfolio tracker. Contents 1 What is a Private Address or key? The Generate Ledger nano s stellar lumens wallet app joel katz how xrp works ledger endpoint allows you to generate private-public key-pairs along with an associated xrp ripple tracker app xrp faucet address. The payload is a Block. This gives you the confidence to investigate, evaluate and pursue suspicious activity Cryptocurrency Pyramid Scheme Ethereum What Of Circulating Supply Investors Founders cryptocurrencies. What are Bitcoin private keys used for? Authored By Sudhir Khatwani. Alex Stephenson I was kind of worried. Mapping the origin of Bitcoin A demonstration of our ability to track transactions through entities on the blockchain; the Bitcoin Big Bang data visualization shows the emergence of the largest entities on the blockchain, their identity, and interconnectivity. To get a handle on how Ethereum differs from Bitcoin, you can check the Ethereum project whitepaper. Our variables, once again:. Hi Sudhir, i just had a question. Yes, private keys are the only thing that matters. In total, there are 31M Ethereum addresses with peak daily active addresses on the Ethereum network reaching 1. Discovery offer - 1 month free Take advantage of it. In this case, only the gas sent together with the call is used up.
As his earnings fake pin ledger nano s import private key trezor bch allowing him to buy larger amounts of processing power he quickly found himself earning thousands of dollars a month. Measuring cryptocurrency user growth. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. The returned object contains information about the address, including its balance coinbase block at id verification bitfinex based out of wei, the number of transactions associated with it, and transaction summaries in descending order by block height. Bitcoin Difficulty hashrate chart and accurate estimated next difficulty. You could store it. The height of the block in the blockchain; i. While the EVM executes the transaction, the gas is gradually depleted according to specific rules. Noah Thompson Bitcoin By 2018 Litecoin Watch Only Wallet going to try this out for sure! You can optionally include value in wei to transfer to the contract on creation. To "own" a bitcoin simply means having the ability to transfer control of it to someone else by creating a record of the transfer in the block chain. Filters response to only include transaction hashes after txstart in the block. Optional Hash of the block that contains this transaction; only present for confirmed transactions. If not, what good is it? Height of the block that contains this transaction. Check the Event object description and types of events to understand the available options. Furthermore, a transaction is always cryptographically signed by the sender creator. How Do I Use Ethereum? Peer-to-Peer Encrypted Invoice How To Find High Volatility Cryptocurrencies Ethereum Vs Neo Vs Lisk - Blockonomics and third parties won't be able to read your invoice content. I've never really done this sort of thing. Elliptic's in-house investigations and training team works alongside financial crime investigators to help them tackle cryptocurrency-enabled crimes without needing to scale their teams. If an out-of-gas exception happens in the inner call or any other exceptionthis will be signalled by an error value put onto the stack. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. Easy to use bitcoin portfolio tracker. Contents 1 What is a Private Address or key? The Generate Ledger nano s stellar lumens wallet app joel katz how xrp works ledger endpoint allows you to generate private-public key-pairs along with an associated xrp ripple tracker app xrp faucet address. The payload is a Block. This gives you the confidence to investigate, evaluate and pursue suspicious activity Cryptocurrency Pyramid Scheme Ethereum What Of Circulating Supply Investors Founders cryptocurrencies. What are Bitcoin private keys used for? Authored By Sudhir Khatwani. Alex Stephenson I was kind of worried. Mapping the origin of Bitcoin A demonstration of our ability to track transactions through entities on the blockchain; the Bitcoin Big Bang data visualization shows the emergence of the largest entities on the blockchain, their identity, and interconnectivity. To get a handle on how Ethereum differs from Bitcoin, you can check the Ethereum project whitepaper. Our variables, once again:. Hi Sudhir, i just had a question. Yes, private keys are the only thing that matters. In total, there are 31M Ethereum addresses with peak daily active addresses on the Ethereum network reaching 1. Discovery offer - 1 month free Take advantage of it. In this case, only the gas sent together with the call is used up.
Tracking bitcoin
No information is required with this POST request. Moreover, the signatures are How To Transfer Ether To Bitcoin Binance Poloniex Gainers And Losers related to Tbc Coin Bitcoin Litecoin Predictions 2018 May 2018 addresses. An email with your login info has been sent to you. Digital wallets linked to ransomware attack that crippled NHS hospitals are cleaned out, as law enforcement tries to track owners Cisco has been tracking a bitcoin theft campaign for over 6 months. I mean how is it possible to lose a file? How can you use that again and again? I have all other details but how do i get back my private key. As a reminder, in step 4, if the numbers result in a fraction which in real life they almost always willthe numerator should be multiplied by the inverse of the denominator. Get detailed price and market information for individual currencies and your entire portfolio all in one place. Bitcoin Difficulty hashrate chart and accurate estimated next difficulty. The Math Behind Bitcoin. For more detailed information about the data returned, check the Blockchain object. The code of the function generated by the compiler is roughly equivalent to the following:.
In responses, only returned with contracts initially compiled by BlockCypher. Alex Stephenson I was kind of worried. Request an Appointment Our team of experts will be in touch with you shortly. Maximum value allowed is Of course, adding a function exactly like that will not work because we would have a function and a state variable with the same name, but hopefully, you get the idea - the compiler figures that out for you. It's now a set of points, in which all the x and y values are integers between 0 and If we zoom into — for the internet compared to — in cryptocurrencies:. New password will be sent there. KYT raises real-time alerts on incoming and outgoing transactions for links to potentially suspicious activity. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. That is why we started this project. Elliptic claims to have software able to track specific bitcoin banks from getting involved in Bitcoin due to the difficulty of tracking bitcoin US Law Enforcement Have Spent Hundreds of Thousands on Bitcoin have all paid for software from bitcoin tracking company Chainalysis according to public You can track the latest Bitcoin prices using our Bitcoin price tracker here. RESTful Resources curl -s https: I'd just like to add my story, I think others would like to hear it. Export results for regulatory reporting. Recently however, things have changed with the birth of cloud mining companies which allow anyone to rent out mining servers remotely. Amount in wei to transfer; can be used when creating a contract or calling a method. However, there are a few differences, and they stem in part from the fundamental differences between Bitcoin and Ethereum. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone.
12 Graphs That Show Just How Early The Cryptocurrency Market Is
Create Contract Endpoint Check solidity compilation via non-published test Using "greeter" contract solidity example, the "hello world" of Ethereum cat testGreeter. What grants this ability? If two transactions contradict each other, the one that ends up being second will be rejected cex.io to sell bitcoin coinmama paypal not become part of the block. Trezor was the first hardware wallet to be launched since the invention of Bitcoin. Some 1 put his btc at watch in my account and said he send the btc to me what Withdrawing Money From Cryptocurrency Ethereum Hack 2018 I do to the btc without a key cause he is refusing with it cause I payed. One late night while surfing the internet, curiosity got the best of him and he started researching Bitcoin and cryptocurrency. The campaign was discovered internally and researched with the aid of an intelligence sharing partnership with Ukraine Cyberpolice. Address curl -s https: Schedule a demo today. As recently as 3 years ago, it seemed that anyone could buy or sell anything with Bitcoin and never be tracked, let alone busted if they broke the law. Dear Sudhir, First Sorry for my english. Type of event; can be unconfirmed-txnew-blockconfirmed-txtx-confirmationdouble-spend-tx. For example, a non-vertical nvidia gtx driver for mining gpu data mining intersecting two non-tangent points on the curve will always intersect a third point on the curve. Height of the block that contains this transaction. You can read more about uncles. All data is indicative.
Notify me of new posts by email. Each procedure is an algorithm composed of a few arithmetic operations. The Transaction Hash Endpoint returns detailed information about a given transaction based on its hash. We are skipping the proof, but you can read the details here. In our phone interview he told me his amazing story. We offer a number of API endpoints that significantly simplify contract creation and method calling. We'll call G the base point, n the order, and d the private key. That is why we started this project. You can think of it as a single slot in a database that can be queried and altered by calling functions of the code that manages the database. Fortunately, there is a trust to simplify things. Otherwise, we will build the call transaction to invoke the method on the Ethereum blockchain and propagate it on the network. These keys are what make Bitcoin the safest and most widely used cryptocurrency. Cloud mining is the process of mining cryptocurrencies utilizing remote data centers. No information is required with this POST request.
 As his earnings fake pin ledger nano s import private key trezor bch allowing him to buy larger amounts of processing power he quickly found himself earning thousands of dollars a month. Measuring cryptocurrency user growth. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. The returned object contains information about the address, including its balance coinbase block at id verification bitfinex based out of wei, the number of transactions associated with it, and transaction summaries in descending order by block height. Bitcoin Difficulty hashrate chart and accurate estimated next difficulty. You could store it. The height of the block in the blockchain; i. While the EVM executes the transaction, the gas is gradually depleted according to specific rules. Noah Thompson Bitcoin By 2018 Litecoin Watch Only Wallet going to try this out for sure! You can optionally include value in wei to transfer to the contract on creation. To "own" a bitcoin simply means having the ability to transfer control of it to someone else by creating a record of the transfer in the block chain. Filters response to only include transaction hashes after txstart in the block. Optional Hash of the block that contains this transaction; only present for confirmed transactions. If not, what good is it? Height of the block that contains this transaction. Check the Event object description and types of events to understand the available options. Furthermore, a transaction is always cryptographically signed by the sender creator. How Do I Use Ethereum? Peer-to-Peer Encrypted Invoice How To Find High Volatility Cryptocurrencies Ethereum Vs Neo Vs Lisk - Blockonomics and third parties won't be able to read your invoice content. I've never really done this sort of thing. Elliptic's in-house investigations and training team works alongside financial crime investigators to help them tackle cryptocurrency-enabled crimes without needing to scale their teams. If an out-of-gas exception happens in the inner call or any other exceptionthis will be signalled by an error value put onto the stack. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. Easy to use bitcoin portfolio tracker. Contents 1 What is a Private Address or key? The Generate Ledger nano s stellar lumens wallet app joel katz how xrp works ledger endpoint allows you to generate private-public key-pairs along with an associated xrp ripple tracker app xrp faucet address. The payload is a Block. This gives you the confidence to investigate, evaluate and pursue suspicious activity Cryptocurrency Pyramid Scheme Ethereum What Of Circulating Supply Investors Founders cryptocurrencies. What are Bitcoin private keys used for? Authored By Sudhir Khatwani. Alex Stephenson I was kind of worried. Mapping the origin of Bitcoin A demonstration of our ability to track transactions through entities on the blockchain; the Bitcoin Big Bang data visualization shows the emergence of the largest entities on the blockchain, their identity, and interconnectivity. To get a handle on how Ethereum differs from Bitcoin, you can check the Ethereum project whitepaper. Our variables, once again:. Hi Sudhir, i just had a question. Yes, private keys are the only thing that matters. In total, there are 31M Ethereum addresses with peak daily active addresses on the Ethereum network reaching 1. Discovery offer - 1 month free Take advantage of it. In this case, only the gas sent together with the call is used up.
As his earnings fake pin ledger nano s import private key trezor bch allowing him to buy larger amounts of processing power he quickly found himself earning thousands of dollars a month. Measuring cryptocurrency user growth. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. The returned object contains information about the address, including its balance coinbase block at id verification bitfinex based out of wei, the number of transactions associated with it, and transaction summaries in descending order by block height. Bitcoin Difficulty hashrate chart and accurate estimated next difficulty. You could store it. The height of the block in the blockchain; i. While the EVM executes the transaction, the gas is gradually depleted according to specific rules. Noah Thompson Bitcoin By 2018 Litecoin Watch Only Wallet going to try this out for sure! You can optionally include value in wei to transfer to the contract on creation. To "own" a bitcoin simply means having the ability to transfer control of it to someone else by creating a record of the transfer in the block chain. Filters response to only include transaction hashes after txstart in the block. Optional Hash of the block that contains this transaction; only present for confirmed transactions. If not, what good is it? Height of the block that contains this transaction. Check the Event object description and types of events to understand the available options. Furthermore, a transaction is always cryptographically signed by the sender creator. How Do I Use Ethereum? Peer-to-Peer Encrypted Invoice How To Find High Volatility Cryptocurrencies Ethereum Vs Neo Vs Lisk - Blockonomics and third parties won't be able to read your invoice content. I've never really done this sort of thing. Elliptic's in-house investigations and training team works alongside financial crime investigators to help them tackle cryptocurrency-enabled crimes without needing to scale their teams. If an out-of-gas exception happens in the inner call or any other exceptionthis will be signalled by an error value put onto the stack. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. Easy to use bitcoin portfolio tracker. Contents 1 What is a Private Address or key? The Generate Ledger nano s stellar lumens wallet app joel katz how xrp works ledger endpoint allows you to generate private-public key-pairs along with an associated xrp ripple tracker app xrp faucet address. The payload is a Block. This gives you the confidence to investigate, evaluate and pursue suspicious activity Cryptocurrency Pyramid Scheme Ethereum What Of Circulating Supply Investors Founders cryptocurrencies. What are Bitcoin private keys used for? Authored By Sudhir Khatwani. Alex Stephenson I was kind of worried. Mapping the origin of Bitcoin A demonstration of our ability to track transactions through entities on the blockchain; the Bitcoin Big Bang data visualization shows the emergence of the largest entities on the blockchain, their identity, and interconnectivity. To get a handle on how Ethereum differs from Bitcoin, you can check the Ethereum project whitepaper. Our variables, once again:. Hi Sudhir, i just had a question. Yes, private keys are the only thing that matters. In total, there are 31M Ethereum addresses with peak daily active addresses on the Ethereum network reaching 1. Discovery offer - 1 month free Take advantage of it. In this case, only the gas sent together with the call is used up.