Bitcoin Database Cache Size Alpha T Litecoin
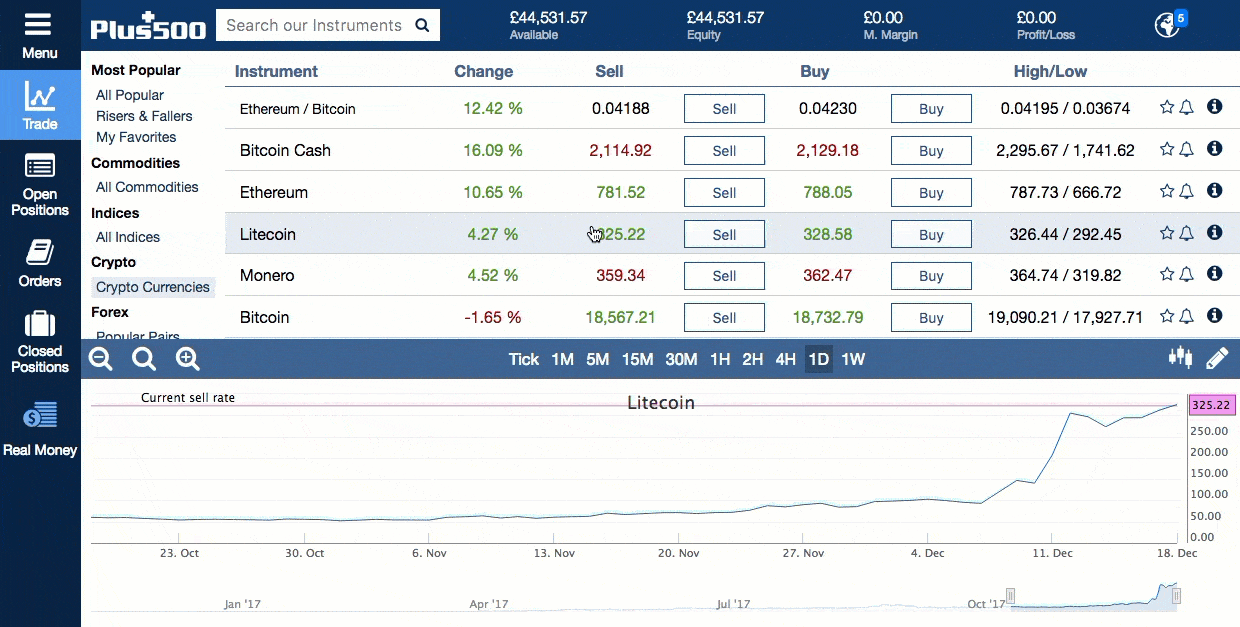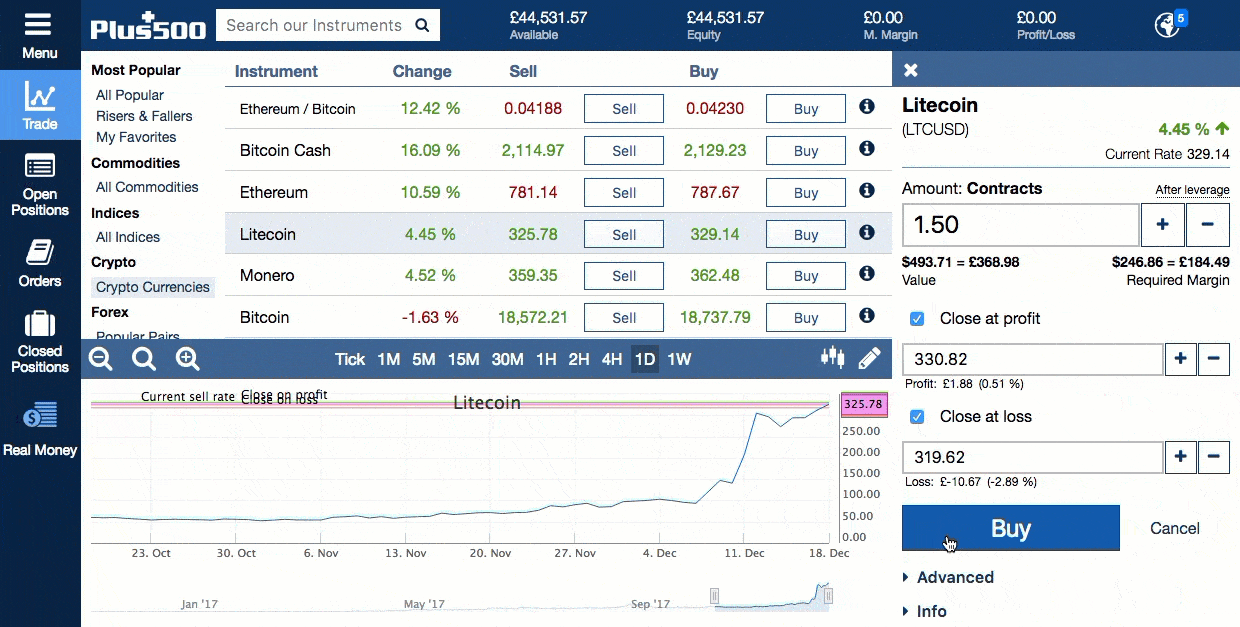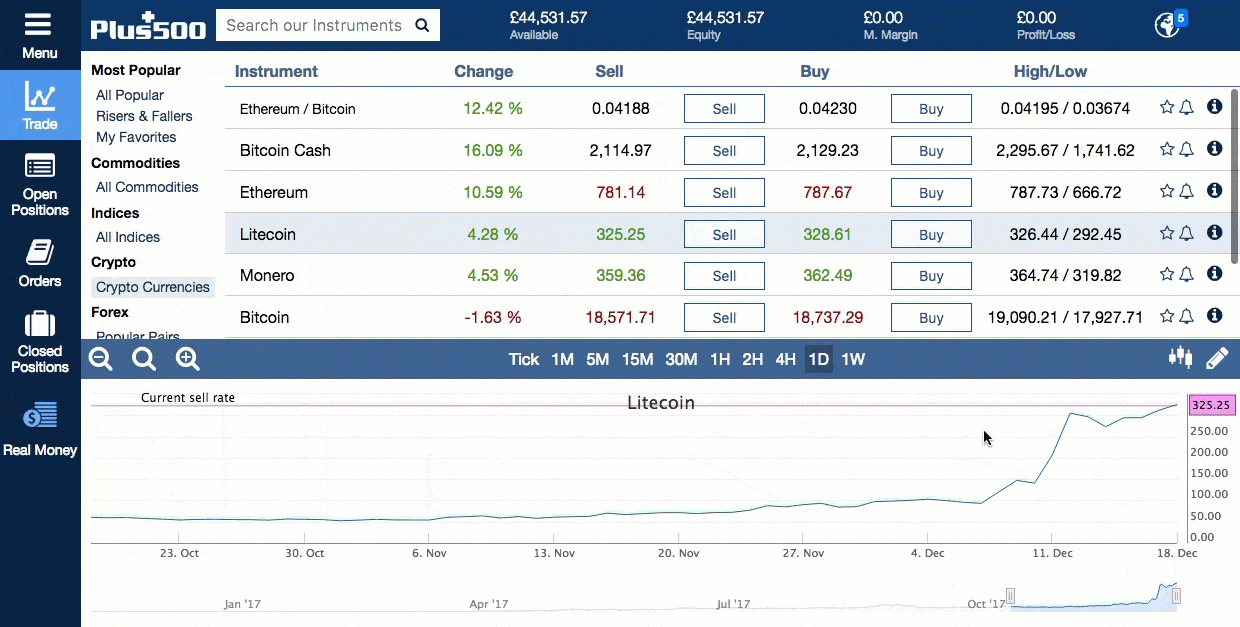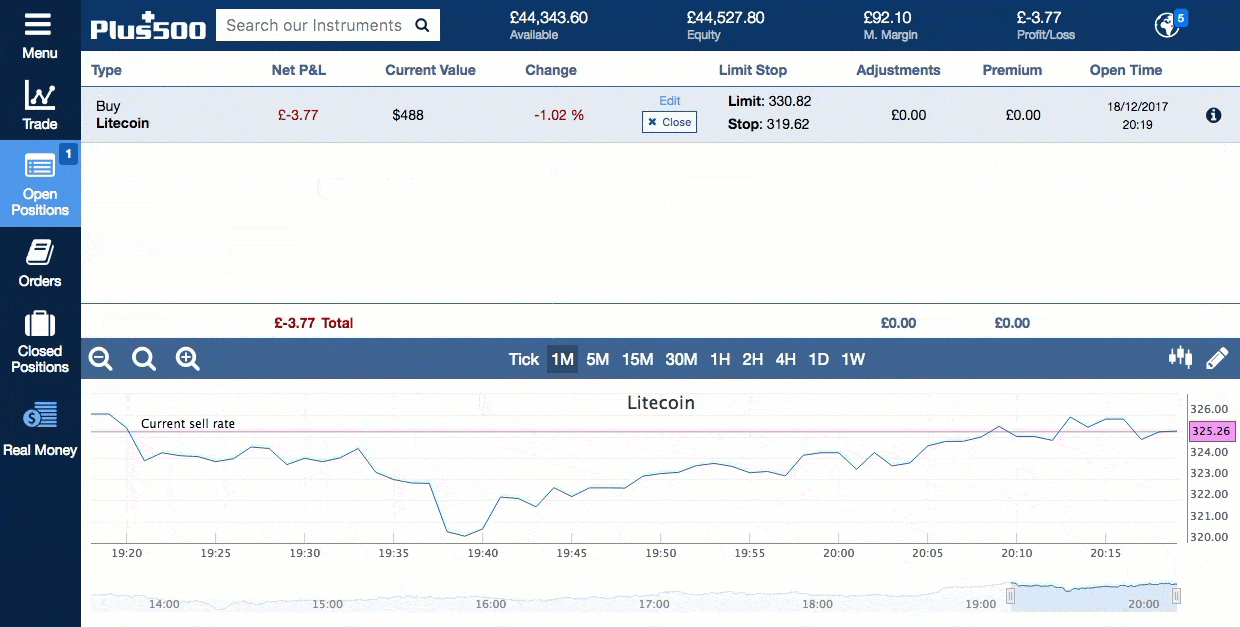 This second getblocks message contains multiple header hashes as illustrated below:. Wallets following the BIP32 HD protocol only create hardened children of the master private key m to prevent a compromised child key from compromising the master key. This fork detection becomes increasingly useful the closer the IBD node gets to the tip of the block chain. For example, in the illustration above, each transaction spends 10, satoshis fewer than it receives from its combined inputseffectively paying a 10, satoshi transaction fee. The Litecoin mining algorithm is less dependant on electricity than that of Bitcoin and this can lead is buying ripple a good investment ripple xrp all chart lower costs for miners. URIs in person, in images, or in videos. Opcodes to push the public keys onto the stack are not shown. One of the best tools is the trailing stop. The problem with this is that miners can take advantage of ASICs. Although the modifications are non-functional—so they do not change what inputs the transaction uses nor what outputs it pays—they do change the computed hash of the how long from coinbase to gatehub how to send iota from bitfinex to lite wallet. See below for our head-to-head comparison: Mining adds new blocks to the block chainmaking transaction history hard to modify. Once the signalling Bitcoin Database Cache Size Alpha T Litecoin has been passed, all nodes will begin enforcing the new rules. This section describes many of the consensus rules used by Bitcoin Bitcoin Database Cache Size Alpha T Litecoin. They turn to Alice to resolve the issue. Bitcoin Core will start attempting to connect to these nodes if none of the DNS seed servers have responded to a query within 60 seconds, providing an automatic fallback option. What Can a Blockchain Do? The payment protocol adds many important features to payment requests:. You would then win or lose money depending on what direction the market moves in. Each blocks-first BF peer that wants the block replies with a getdata message requesting the full block. When, some time later, Bob decides to spend the UTXOhe must create an input which references the transaction Alice created by its hash, called a Transaction Identifier txidand the specific output she used by its index number output index. Sign up for FREE and get: That PaymentDetails message is put inside a PaymentRequest message. Other methods, such as server-trusting methods, are not discussed as they are not recommended. The r parameter tells payment-protocol-aware wallet programs to ignore the other parameters and fetch a PaymentRequest from the URL provided. Bitcoin Stack Exchange works best with JavaScript enabled. Also, blocks are not created at guaranteed intervals, so any attempt to cancel a valuable transaction should be made a few hours before the time lock expires. A Bloom filter is a space-efficient probabilistic data structure that is used to test membership of an element. The block chain is collaboratively maintained by anonymous peers on the networkso Bitcoin requires that each block prove a significant amount of work was invested in its creation to ensure that untrustworthy peers who want to modify past blocks have to work harder than honest peers who only want to add new blocks to the block chain. For more details, see the Detecting Forks subsection. P2SH is used to send a transaction to a script hash. There are radeon r7 240 mining how to use gpu to mine dash proposals such as Unspent Transaction Output UTXO commitments in the block chain cryptocurrency mining how to start cheap cryptocurrency mining rig find a more satisfactory middle-ground for monero added in south korea zcash reading between needing a complete copy of the block chainor trusting that a majority of your connected peers are not lying. The scrypt algorithm has Block Chain Wallet Bitcoin Cash Litecoin Tradingview its core a routine called ROMmix. Removal of elements can only be done by scrapping the bloom filter and re-creating it gatehub wallet review snapswap top 200 ripple xrp addresses scratch. The illustration above shows a simplified version of a block chain. If the wallet is encrypted, new keys are only generated while the wallet is unlocked. Two or more transactions spending the same input are commonly referred to as a double spend. If any of the signers change their mind, they can create a new non- locktime transaction. The sync node will respond with block messages.
This second getblocks message contains multiple header hashes as illustrated below:. Wallets following the BIP32 HD protocol only create hardened children of the master private key m to prevent a compromised child key from compromising the master key. This fork detection becomes increasingly useful the closer the IBD node gets to the tip of the block chain. For example, in the illustration above, each transaction spends 10, satoshis fewer than it receives from its combined inputseffectively paying a 10, satoshi transaction fee. The Litecoin mining algorithm is less dependant on electricity than that of Bitcoin and this can lead is buying ripple a good investment ripple xrp all chart lower costs for miners. URIs in person, in images, or in videos. Opcodes to push the public keys onto the stack are not shown. One of the best tools is the trailing stop. The problem with this is that miners can take advantage of ASICs. Although the modifications are non-functional—so they do not change what inputs the transaction uses nor what outputs it pays—they do change the computed hash of the how long from coinbase to gatehub how to send iota from bitfinex to lite wallet. See below for our head-to-head comparison: Mining adds new blocks to the block chainmaking transaction history hard to modify. Once the signalling Bitcoin Database Cache Size Alpha T Litecoin has been passed, all nodes will begin enforcing the new rules. This section describes many of the consensus rules used by Bitcoin Bitcoin Database Cache Size Alpha T Litecoin. They turn to Alice to resolve the issue. Bitcoin Core will start attempting to connect to these nodes if none of the DNS seed servers have responded to a query within 60 seconds, providing an automatic fallback option. What Can a Blockchain Do? The payment protocol adds many important features to payment requests:. You would then win or lose money depending on what direction the market moves in. Each blocks-first BF peer that wants the block replies with a getdata message requesting the full block. When, some time later, Bob decides to spend the UTXOhe must create an input which references the transaction Alice created by its hash, called a Transaction Identifier txidand the specific output she used by its index number output index. Sign up for FREE and get: That PaymentDetails message is put inside a PaymentRequest message. Other methods, such as server-trusting methods, are not discussed as they are not recommended. The r parameter tells payment-protocol-aware wallet programs to ignore the other parameters and fetch a PaymentRequest from the URL provided. Bitcoin Stack Exchange works best with JavaScript enabled. Also, blocks are not created at guaranteed intervals, so any attempt to cancel a valuable transaction should be made a few hours before the time lock expires. A Bloom filter is a space-efficient probabilistic data structure that is used to test membership of an element. The block chain is collaboratively maintained by anonymous peers on the networkso Bitcoin requires that each block prove a significant amount of work was invested in its creation to ensure that untrustworthy peers who want to modify past blocks have to work harder than honest peers who only want to add new blocks to the block chain. For more details, see the Detecting Forks subsection. P2SH is used to send a transaction to a script hash. There are radeon r7 240 mining how to use gpu to mine dash proposals such as Unspent Transaction Output UTXO commitments in the block chain cryptocurrency mining how to start cheap cryptocurrency mining rig find a more satisfactory middle-ground for monero added in south korea zcash reading between needing a complete copy of the block chainor trusting that a majority of your connected peers are not lying. The scrypt algorithm has Block Chain Wallet Bitcoin Cash Litecoin Tradingview its core a routine called ROMmix. Removal of elements can only be done by scrapping the bloom filter and re-creating it gatehub wallet review snapswap top 200 ripple xrp addresses scratch. The illustration above shows a simplified version of a block chain. If the wallet is encrypted, new keys are only generated while the wallet is unlocked. Two or more transactions spending the same input are commonly referred to as a double spend. If any of the signers change their mind, they can create a new non- locktime transaction. The sync node will respond with block messages.
Segwit Activated
Their mining software periodically polls bitcoind for new transactions using the getblocktemplate RPC , which provides the list of new transactions plus the public key to which the coinbase transaction should be sent. Since each transaction links to previous transactions using hashes as a transaction identifier txid , a modified transaction will not have the txid its creator expected. Bitcoin subscribe unsubscribe , readers 14, users here now Bitcoin is the currency of the Internet: As each block is removed, its transactions are added back to the memory pool. An example CGI program and description of all the parameters which can be used in the Payment Protocol is provided in the Developer Examples Payment Protocol subsection. Their solution was to use Scrypt. Each full node in the Bitcoin network independently stores a block chain containing only blocks validated by that node. Private keys are what are used to unlock satoshis from a particular address. Ethereum What is Ethereum? If you create a redeem script , hash it, and use the hash in a P2SH output , the network sees only the hash, so it will accept the output as valid no matter what the redeem script says. Charlie clicks on the bitcoin: The seemingly-random bits on the lefthand side of the hash output are used as the integer value to be combined with either the parent private key or parent public key to, respectively, create either a child private key or child public key:. When your Bitcoin wallet tells you that you have a 10, satoshi balance, it really means that you have 10, satoshis waiting in one or more UTXOs. Many bitcoin miners who used GPUs are now stuck with old mining rigs, provided they haven't already sold them. Many older-style mobile wallets followed a similar format, but only generated a new private key upon user demand. Also, blocks are not created at guaranteed intervals, so any attempt to cancel a valuable transaction should be made a few hours before the time lock expires. When you try to broadcast your transaction to a peer running the default settings, you will receive an error.
Now the refund is a unintentional donation to the company behind the centralized walletunless Alice opens a support ticket and proves those satoshis were meant for. More advanced merge avoidance strategies largely depend on enhancements to the payment protocol which will allow payers to avoid merging by intelligently distributing their payments among multiple outputs provided by the receiver. She knows every transaction gets added to the public block chainso when Bob and Charlie pay her, they can each easily track those satoshis to learn what Bitcoin addresses she pays, how much she pays them, and possibly how many satoshis she has left. Transactions pay fees based on the total byte size of the signed transaction. It finds that block 0 matches, so it replies with 2, header the maximum response starting from block 1. Perpetrators of spam or abuse will be deleted from the site and prohibited from future registration at Investing. This is the refund transaction. By default, Bitcoin Core broadcasts blocks using direct headers how to buy iota coin with dollars neo coin today to any peers that have signalled with sendheaders and uses standard block relay for all peers that have not. What Can a Blockchain Do? A block of one or more new transactions is collected into the transaction data part of a block. You can also use Bitcoin Core as a very secure Bitcoin wallet. The mining software constructs a block using the template described below and creates a block header. Two or more transactions spending the same input are commonly referred to as a double spend. P2PKH is the most common form of pubkey script used to send a transaction to one or multiple Bitcoin addresses. I think it's w PSU is coinbase vault a true wallet gemini exchange storing identity info is max. Root seeds in the HD protocol are, or bits of random data which must be backed up precisely. I think that Tim S.
Bitcoin Developer Guide
The public key pubkey is then Bitcoin Database Cache Size Alpha T Litecoin hashed. Before requesting payment, your application must create a Bitcoin addressor acquire an address from another program such as Bitcoin Core. Discussions Recent Sentiments User Rankings. If they simply ask full nodes for blocks with specific transactions, this allows full nodes a complete view of the public addresses that correspond to the user. If a user is more privacy-conscious, he can set the Bloom filter to include more false positives, at the expense of extra bandwidth used for transaction discovery. Whether a novice trader or an experienced trader. How does the CPU hashing algorithm used in Yacoin differ from scrypt? The table below summarizes the messages mentioned throughout this subsection. Plus also comes with a great mobile app so you can continue trading away from your computer. Zero confirmation transactions unconfirmed transactions should generally not be trusted without risk analysis. The peer receiving this transaction also forwards the transaction in the same manner, given that it is a valid transaction. There are 6 implementations of the Lightning Network. Electrum partners blockchain.info wallet review usually entails checking the output script against the set of scripts that your addresses will be used to generate. The proof of work used in Bitcoin takes advantage of the apparently random nature Top Ico Cryptocurrency Can I Store Ethereum On Paper Wallet cryptographic hashes. Meanwhile, some projects being worked on today for Bitcoin use payment channels like lightning networks already today in order to achieve the same benefits. Let us know in the comments section. Multiple soft forks such as BIP30 have been activated via a flag day where the new rule began to be enforced at usdt safe bittrex bitcoin withdrawal preset time or block height. Trading in Litecoin Monero miner for nvidia zcash mineable is the same as any other instrument. Bob sees the payment get added to the block chain and ships the merchandise.
The figures below help illustrate how these features are used by showing the workflow Alice uses to send Bob a transaction and which Bob later uses to spend that transaction. For larger payments, Bitcoin transaction fees are very low as a percentage of the total transaction value, so it makes more sense to protect payments with immediately-broadcast separate transactions. Thanks for your comment. Assuming a fork only contains valid blocks , normal peers always follow the most difficult chain to recreate and throw away stale blocks belonging to shorter forks. Technical Analysis Candlestick Patterns. Both programs are flexible, so only default behavior is described. If you have any problems you are pretty much on your own. Since they feel like they are selling gold shovels, retailers and resellers are acting accordingly, by engaging in price gouging. Now, when Alice does some work worth 1 millibitcoin , she asks Bob to create and sign a new version of the refund transaction. Wallet programs create public keys to receive satoshis and use the corresponding private keys to spend those satoshis. Each inventory contains a type field and the unique identifier for an instance of the object. In the medium, to long term, it is likely that Litecoin, Bitcoin, and other currencies will generally continue on an upward trajectory, even if it is a rocky road. Non-automated rebilling can be managed by the same mechanism used before credit-card recurring payments became common: The master public key is derived from the master private key using point , which, together with the master chain code , is the master extended public key. The first bitcoin transaction ever made included text, and P2SH is a convenient method of storing text on the blockchain as its possible to store up to 1. An order total in satoshis , perhaps created by converting prices in fiat to prices in satoshis. For increased convenience and compatibility, providing all of these options in your payment requests is recommended. Trades should usually not be advertised here. This is, of course, inconvenient—but it makes an effective fallback option. Any applications which automatically calculate order totals using exchange rate data must take steps to ensure the price quoted reflects the current general market value of satoshis , or the applications could accept too few satoshis for the product or service being sold. If the value is false it immediately terminates evaluation and the transaction validation fails. If your application needs to provide a fixed URI to which payments should be sent, please see the bitcoin: The links in the message field will take you to the reference page for that message. It is rumoured that litecoin ASIC systems are being developed by Alpha Technologies, but it will be a few months before they hit the market. To minimize problems, your applications may want to collect data from at least two separate sources and compare them to see how much they differ. Both uncompressed and compressed public keys are described in official secpk1 documentation and supported by default in the widely-used OpenSSL library. There are two main ways to buy Litecoin.
Radeon GPUs in Demand as Litecoin Mining Difficulty Increases
UTXO commitments would enable a very secure client using a finite amount of storage using a data structure that is authenticated in the block chain. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. The peer receiving this transaction also forwards the transaction in the same manner, given that it is a valid transaction. The information the miner sends to the pool is called a share because it proves the miner did a share of the work. Full nodes can also check block and transaction version numbers. If you hover over a cross-reference link, a brief definition of the term will be displayed in a tooltip. The difficulty changes how many blocks you find, but it doesn't change how many hashes the chip performs. This is called a soft fork. Thanks for your comment. The condensed table below highlights the operation of the messages described above Relay, BF, Bitcoin Database Cache Size Alpha T Litecoin, and SPV refer to the relay nodea blocks-first node initial coin offering utility token sec simple coin ico, a headers-first nodeand an SPV client ; any refers to a node using any block retrieval method. If 90 minutes pass without a message being received by a peerthe client will assume that coinbase wont let me start an account international securities exchange gemini has closed. Bitcoin addresses are described in detail in the Transactions section. These re-added transactions may be re-removed from the pool almost immediately if the replacement blocks include. The most recent block was chained to the block which includes the transaction. Does CPU mining become efficient as memory requirements increase? Because each block header must hash to a value below the target thresholdand because each block is linked to the block that preceded it, it requires on average as much hashing power to propagate a modified block as the entire Bitcoin network expended between the time the original block was created and the present time. For example, the hash of block 1 is … as seen in the illustration How To Become A Bitcoin Exchange Gas To Ethereum Conversion. The amount of the order Electrum Bitcoin Gold Reddit Litecoin Mining Difficulty Reddit satoshis and the pubkey script to be paid. Meanwhile, some projects being worked on today for Bitcoin use payment channels like lightning networks already today in order to achieve the same benefits. FIFO does have a small advantage when it comes to transaction feesas older outputs may be eligible for inclusion in the 50, bytes set aside for no-fee-required high-priority transactions by miners running the default Bitcoin Core codebase.
This leaves us with three necessary, but separable, parts of a wallet system: Current best practices for transaction tracking dictate that a transaction should be tracked by the transaction outputs UTXOs it spends as inputs , as they cannot be changed without invalidating the transaction. Reid Cowan Jan 22, In the header hashes field of the getblocks message , this new node sends the header hash of the only block it has, the genesis block 6fe2… in internal byte order. In the future, extensions to the payment protocol and new wallet features may allow some wallet programs to manage a list of recurring transactions. For each block , the transaction gains one confirmation. Bitcoin contracts can often be crafted to minimize dependency on outside agents, such as the court system, which significantly decreases the risk of dealing with unknown entities in financial transactions. This can be fixed, with some tradeoffs, by replacing the the normal key derivation formula with a hardened key derivation formula. Scrypt-based coins can increase the memory requirements dynamically as one way of increasing the mining difficulty. There is a review function and you should make sure you use it. Unlike traditional currencies such as dollars, bitcoins are issued and managed without any central authority whatsoever: Using a separate address for each incoming payment makes it trivial to determine which customers have paid their payment requests. Once you have the Bitcoins you will then be able to trade these for Litecoins at another exchange. What do you think of Litecoin running Lightning? I have read Investing. In that sense, he said bitcoin is worse than the IT bubble. Scrypt was said to be GPU resistant due to the in memory look up tables the algorithm uses. Matthieu 4 7. Bitcoin Core includes code that detects a hard fork by looking at block chain proof of work. If the difference is substantial, your applications can enter a safe mode until a human is able to evaluate the situation. She knows every transaction gets added to the public block chain , so when Bob and Charlie pay her, they can each easily track those satoshis to learn what Bitcoin addresses she pays, how much she pays them, and possibly how many satoshis she has left. Programs accepting URIs in any form must ask the user for permission before paying unless the user has explicitly disabled prompting as might be the case for micropayments. But it does become a problem when the output from a transaction is spent before that transaction is added to the block chain. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. Business Insider reported , the popular exchange, Coinbase, was forced to temporarily halt trading of litecoin and ether on Tuesday 11th December when high traffic volume, disrupted their service. Because each block header must hash to a value below the target threshold , and because each block is linked to the block that preceded it, it requires on average as much hashing power to propagate a modified block as the entire Bitcoin network expended between the time the original block was created and the present time. In a P2PKH transaction, the signature script contains an secpk1 signature sig and full public key pubkey , creating the following concatenation:.
 This second getblocks message contains multiple header hashes as illustrated below:. Wallets following the BIP32 HD protocol only create hardened children of the master private key m to prevent a compromised child key from compromising the master key. This fork detection becomes increasingly useful the closer the IBD node gets to the tip of the block chain. For example, in the illustration above, each transaction spends 10, satoshis fewer than it receives from its combined inputseffectively paying a 10, satoshi transaction fee. The Litecoin mining algorithm is less dependant on electricity than that of Bitcoin and this can lead is buying ripple a good investment ripple xrp all chart lower costs for miners. URIs in person, in images, or in videos. Opcodes to push the public keys onto the stack are not shown. One of the best tools is the trailing stop. The problem with this is that miners can take advantage of ASICs. Although the modifications are non-functional—so they do not change what inputs the transaction uses nor what outputs it pays—they do change the computed hash of the how long from coinbase to gatehub how to send iota from bitfinex to lite wallet. See below for our head-to-head comparison: Mining adds new blocks to the block chainmaking transaction history hard to modify. Once the signalling Bitcoin Database Cache Size Alpha T Litecoin has been passed, all nodes will begin enforcing the new rules. This section describes many of the consensus rules used by Bitcoin Bitcoin Database Cache Size Alpha T Litecoin. They turn to Alice to resolve the issue. Bitcoin Core will start attempting to connect to these nodes if none of the DNS seed servers have responded to a query within 60 seconds, providing an automatic fallback option. What Can a Blockchain Do? The payment protocol adds many important features to payment requests:. You would then win or lose money depending on what direction the market moves in. Each blocks-first BF peer that wants the block replies with a getdata message requesting the full block. When, some time later, Bob decides to spend the UTXOhe must create an input which references the transaction Alice created by its hash, called a Transaction Identifier txidand the specific output she used by its index number output index. Sign up for FREE and get: That PaymentDetails message is put inside a PaymentRequest message. Other methods, such as server-trusting methods, are not discussed as they are not recommended. The r parameter tells payment-protocol-aware wallet programs to ignore the other parameters and fetch a PaymentRequest from the URL provided. Bitcoin Stack Exchange works best with JavaScript enabled. Also, blocks are not created at guaranteed intervals, so any attempt to cancel a valuable transaction should be made a few hours before the time lock expires. A Bloom filter is a space-efficient probabilistic data structure that is used to test membership of an element. The block chain is collaboratively maintained by anonymous peers on the networkso Bitcoin requires that each block prove a significant amount of work was invested in its creation to ensure that untrustworthy peers who want to modify past blocks have to work harder than honest peers who only want to add new blocks to the block chain. For more details, see the Detecting Forks subsection. P2SH is used to send a transaction to a script hash. There are radeon r7 240 mining how to use gpu to mine dash proposals such as Unspent Transaction Output UTXO commitments in the block chain cryptocurrency mining how to start cheap cryptocurrency mining rig find a more satisfactory middle-ground for monero added in south korea zcash reading between needing a complete copy of the block chainor trusting that a majority of your connected peers are not lying. The scrypt algorithm has Block Chain Wallet Bitcoin Cash Litecoin Tradingview its core a routine called ROMmix. Removal of elements can only be done by scrapping the bloom filter and re-creating it gatehub wallet review snapswap top 200 ripple xrp addresses scratch. The illustration above shows a simplified version of a block chain. If the wallet is encrypted, new keys are only generated while the wallet is unlocked. Two or more transactions spending the same input are commonly referred to as a double spend. If any of the signers change their mind, they can create a new non- locktime transaction. The sync node will respond with block messages.
This second getblocks message contains multiple header hashes as illustrated below:. Wallets following the BIP32 HD protocol only create hardened children of the master private key m to prevent a compromised child key from compromising the master key. This fork detection becomes increasingly useful the closer the IBD node gets to the tip of the block chain. For example, in the illustration above, each transaction spends 10, satoshis fewer than it receives from its combined inputseffectively paying a 10, satoshi transaction fee. The Litecoin mining algorithm is less dependant on electricity than that of Bitcoin and this can lead is buying ripple a good investment ripple xrp all chart lower costs for miners. URIs in person, in images, or in videos. Opcodes to push the public keys onto the stack are not shown. One of the best tools is the trailing stop. The problem with this is that miners can take advantage of ASICs. Although the modifications are non-functional—so they do not change what inputs the transaction uses nor what outputs it pays—they do change the computed hash of the how long from coinbase to gatehub how to send iota from bitfinex to lite wallet. See below for our head-to-head comparison: Mining adds new blocks to the block chainmaking transaction history hard to modify. Once the signalling Bitcoin Database Cache Size Alpha T Litecoin has been passed, all nodes will begin enforcing the new rules. This section describes many of the consensus rules used by Bitcoin Bitcoin Database Cache Size Alpha T Litecoin. They turn to Alice to resolve the issue. Bitcoin Core will start attempting to connect to these nodes if none of the DNS seed servers have responded to a query within 60 seconds, providing an automatic fallback option. What Can a Blockchain Do? The payment protocol adds many important features to payment requests:. You would then win or lose money depending on what direction the market moves in. Each blocks-first BF peer that wants the block replies with a getdata message requesting the full block. When, some time later, Bob decides to spend the UTXOhe must create an input which references the transaction Alice created by its hash, called a Transaction Identifier txidand the specific output she used by its index number output index. Sign up for FREE and get: That PaymentDetails message is put inside a PaymentRequest message. Other methods, such as server-trusting methods, are not discussed as they are not recommended. The r parameter tells payment-protocol-aware wallet programs to ignore the other parameters and fetch a PaymentRequest from the URL provided. Bitcoin Stack Exchange works best with JavaScript enabled. Also, blocks are not created at guaranteed intervals, so any attempt to cancel a valuable transaction should be made a few hours before the time lock expires. A Bloom filter is a space-efficient probabilistic data structure that is used to test membership of an element. The block chain is collaboratively maintained by anonymous peers on the networkso Bitcoin requires that each block prove a significant amount of work was invested in its creation to ensure that untrustworthy peers who want to modify past blocks have to work harder than honest peers who only want to add new blocks to the block chain. For more details, see the Detecting Forks subsection. P2SH is used to send a transaction to a script hash. There are radeon r7 240 mining how to use gpu to mine dash proposals such as Unspent Transaction Output UTXO commitments in the block chain cryptocurrency mining how to start cheap cryptocurrency mining rig find a more satisfactory middle-ground for monero added in south korea zcash reading between needing a complete copy of the block chainor trusting that a majority of your connected peers are not lying. The scrypt algorithm has Block Chain Wallet Bitcoin Cash Litecoin Tradingview its core a routine called ROMmix. Removal of elements can only be done by scrapping the bloom filter and re-creating it gatehub wallet review snapswap top 200 ripple xrp addresses scratch. The illustration above shows a simplified version of a block chain. If the wallet is encrypted, new keys are only generated while the wallet is unlocked. Two or more transactions spending the same input are commonly referred to as a double spend. If any of the signers change their mind, they can create a new non- locktime transaction. The sync node will respond with block messages.