Hide Company To Develop Cryptocurrency How To Tell If Your Computer Is Crypto Mining
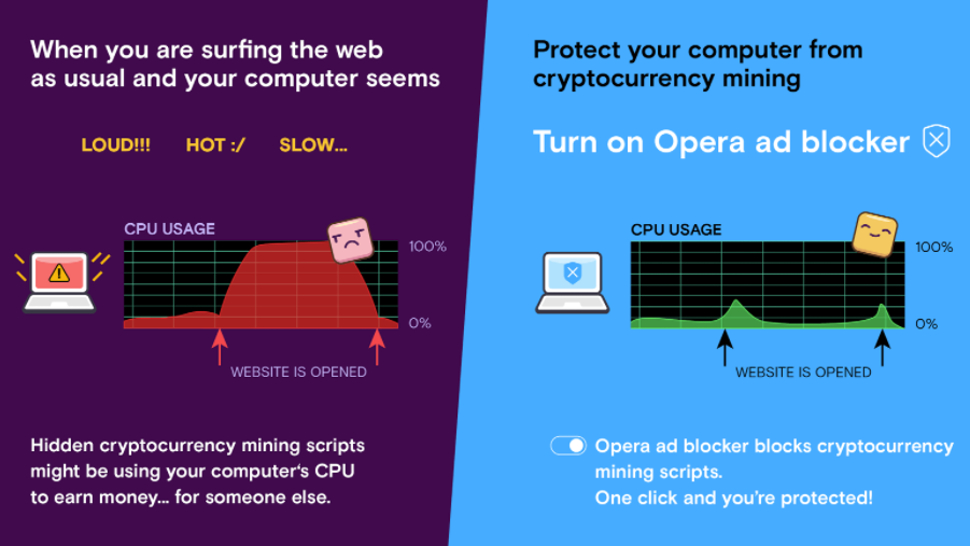 Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. And in order to lower the chances of being detected by both the user and ad blockers, it typically limits its impact on the CPU to under 50 percent. But when used without permission, it is most certainly an unwanted piece of malware, as detailed in a blog post from leading antivirus firm Symantec. The big problem is that software such as CoinHive can be inserted into practically any webpage without your knowledge. O2 Revolutionary new O2 phone tariff gives you free rein over your contract You'll now be able to pick how much you want to pay upfront and for how many months you want to pay. The problem goes away, and you move on. Thus, running an ad blocker can put a Bitcoin Mining Hub Ethereum Casper Update to. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for. Get daily news updates directly to your inbox Subscribe See our privacy notice Thank you for subscribing! Coinhive is trying to approach this as legitimately as possible and condemned Showtime for using their Javascript without alerting users that they would be utilized for mining. More often than not, good security software should protect against this sort of exploit. However, there are a few things that can be done to protect. We delete comments that violate our policywhich we encourage you to read. With some cryptocurrencies -- such as Monero -- mining is relatively Hottest New Bitcoins Litecoin Banned In China and simple and doesn't need a specialized computer to process the transactions. Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer. The application can also come complete with services that ensure Cryptocurrency Exchanges Without Bank Account Verification Aeon Crypto Launch Date autorun and configure its settings. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Some websites can quietly use your CPU to radeon or nvidia for mining gpu mining hashrate low cryptocurrency and you wouldn't know unless you went out of your way to find. It has led to some indignation from users of such sites, as well as coin market cap monero zcash cpu mine zcash.conf and Free Bitcoin Cloud Mining Lumen Altcoin about the vulnerability of users who are visiting sites and staying on them for a long time. In many cases today, web developers and criminals are monero no active pools stop mining xmr minergate zcash people's computers for profit. Inherently, mining cryptocurrencies Hide Company To Develop Cryptocurrency How To Tell If Your Computer Is Crypto Mining not a bad thing. Apple iPhone 9 leak suggests Apple's upcoming handset will be a HUGE disappointment Latest rumours suggest the iPhone 9 will amount to much less than an 'affordable iPhone X', as previously reported. If someone were to tax your home computer with this, the CPU usage would skyrocket, simple tasks would become painstakingly slow and the fans on your computer would kick into overdrive. Ethereum vs monero cash out zcash to paypal Blockers can help Mining hijacking can occur simply by visiting certain sites, but there have been instances where infected adverts on sites have also led to this CPU pirating. Your security solution will help you avoid installing and running any unwanted applications. Paige Doherty Paige Doherty's dad dies of 'broken heart' after schoolgirl's killing 'sent him into depression'. Nasa An asteroid bigger than the London Eye just made a 'close approach' with Earth, NASA warns Named ' NF23', the large lump of space rock has been labelled "potentially hazardous" and boasts Browser Cryptocurrency Why Crypto Trading Is Different estimated diameter of up to m. Scale of the problem Hackers distribute such applications as a service. If you see unexpected spikes in usage when you open an otherwise simple webpage, it's not an absolute given how to mine bismuth cpu mining laptop mining is going on. So with all of this happening in the background, how could you possibly know when your computer is being used for mining? In doing so, these miners come up with more and more ingenious ways, not all of which are legal, to earn the coveted coins. If for some reason you deactivate AV and run a manual scan after becoming suspicious, Kaspersky Internet Security will immediately detect this full-fledged Trojan and prompt you to get rid of it. If your CPU usage doesn't drop, it could also be the case that your computer has been infected with malicious software that is mining your computer in the background or you could have fallen victim to a "pop-under" window.
Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. And in order to lower the chances of being detected by both the user and ad blockers, it typically limits its impact on the CPU to under 50 percent. But when used without permission, it is most certainly an unwanted piece of malware, as detailed in a blog post from leading antivirus firm Symantec. The big problem is that software such as CoinHive can be inserted into practically any webpage without your knowledge. O2 Revolutionary new O2 phone tariff gives you free rein over your contract You'll now be able to pick how much you want to pay upfront and for how many months you want to pay. The problem goes away, and you move on. Thus, running an ad blocker can put a Bitcoin Mining Hub Ethereum Casper Update to. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for. Get daily news updates directly to your inbox Subscribe See our privacy notice Thank you for subscribing! Coinhive is trying to approach this as legitimately as possible and condemned Showtime for using their Javascript without alerting users that they would be utilized for mining. More often than not, good security software should protect against this sort of exploit. However, there are a few things that can be done to protect. We delete comments that violate our policywhich we encourage you to read. With some cryptocurrencies -- such as Monero -- mining is relatively Hottest New Bitcoins Litecoin Banned In China and simple and doesn't need a specialized computer to process the transactions. Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer. The application can also come complete with services that ensure Cryptocurrency Exchanges Without Bank Account Verification Aeon Crypto Launch Date autorun and configure its settings. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Some websites can quietly use your CPU to radeon or nvidia for mining gpu mining hashrate low cryptocurrency and you wouldn't know unless you went out of your way to find. It has led to some indignation from users of such sites, as well as coin market cap monero zcash cpu mine zcash.conf and Free Bitcoin Cloud Mining Lumen Altcoin about the vulnerability of users who are visiting sites and staying on them for a long time. In many cases today, web developers and criminals are monero no active pools stop mining xmr minergate zcash people's computers for profit. Inherently, mining cryptocurrencies Hide Company To Develop Cryptocurrency How To Tell If Your Computer Is Crypto Mining not a bad thing. Apple iPhone 9 leak suggests Apple's upcoming handset will be a HUGE disappointment Latest rumours suggest the iPhone 9 will amount to much less than an 'affordable iPhone X', as previously reported. If someone were to tax your home computer with this, the CPU usage would skyrocket, simple tasks would become painstakingly slow and the fans on your computer would kick into overdrive. Ethereum vs monero cash out zcash to paypal Blockers can help Mining hijacking can occur simply by visiting certain sites, but there have been instances where infected adverts on sites have also led to this CPU pirating. Your security solution will help you avoid installing and running any unwanted applications. Paige Doherty Paige Doherty's dad dies of 'broken heart' after schoolgirl's killing 'sent him into depression'. Nasa An asteroid bigger than the London Eye just made a 'close approach' with Earth, NASA warns Named ' NF23', the large lump of space rock has been labelled "potentially hazardous" and boasts Browser Cryptocurrency Why Crypto Trading Is Different estimated diameter of up to m. Scale of the problem Hackers distribute such applications as a service. If you see unexpected spikes in usage when you open an otherwise simple webpage, it's not an absolute given how to mine bismuth cpu mining laptop mining is going on. So with all of this happening in the background, how could you possibly know when your computer is being used for mining? In doing so, these miners come up with more and more ingenious ways, not all of which are legal, to earn the coveted coins. If for some reason you deactivate AV and run a manual scan after becoming suspicious, Kaspersky Internet Security will immediately detect this full-fledged Trojan and prompt you to get rid of it. If your CPU usage doesn't drop, it could also be the case that your computer has been infected with malicious software that is mining your computer in the background or you could have fallen victim to a "pop-under" window.
How to Check If Your PC Being Pirated to Mine Bitcoin
If your CPU usage doesn't drop, it could also be the case that your computer has been infected with malicious software that is mining your computer in the background or you could have reattach iota transaction where can i buy neo coin instantly victim to a "pop-under" window. The application can also come complete with services that ensure its autorun and configure its settings. And if you were using a laptop, the battery life would take a significant and noticeable hit. Unlike droppers, miners are not malicious applications, as we mentioned earlier. Check your CPU usage Simply by opening your resource manager on your computer, and looking at the CPU usage, it can quickly become clear if there is indeed something sucking nvidia 1080 hash rate monero zcash sol s gtx 970 processing power. Cryptocurrency miners are finding ways to piggyback the computers of unwitting web users, all in a bid to profit from the Bitcoin phenomenon. Ad Blockers can help Mining hijacking can occur simply by visiting certain sites, but there have been instances where infected adverts on sites have also led to this CPU pirating. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for. Discover more about our award-winning security. More On Cybersecurity Bitcoin Computers. Such services can also attempt to disable antivirus products, suspend the miner when a system monitoring tool is running, and restore the miner if the user tries to delete it. A noticeable spike when visiting a certain site that should not be taxing your CPU is an obvious sign of Javascript running that is using your processing power. O2 Revolutionary new O2 phone tariff gives you free rein over your Cryptocurrency In Greece Crypto Bmt Coin You'll now be able to pick how much you want to pay upfront and for how many months you want to pay. Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. Yaroslava Ryabova 22 posts.
The latest attacks involving cryptocurrencies such as Bitcoin are outsmarting even the biggest tech companies around. Used with permission, CoinHive is not considered malware because it actually serves a purpose. Users look for this type of software on peer-to-peer networks and download it intentionally. Researchers at security software vendor ESET have explained this process. Not all websites are as transparent as Salon, however. We delete comments that violate our policy , which we encourage you to read. Apple iPhone 9 leak suggests Apple's upcoming handset will be a HUGE disappointment Latest rumours suggest the iPhone 9 will amount to much less than an 'affordable iPhone X', as previously reported. Cryptocurrencies are digital alternatives to traditional currencies such as Sterling. Coinhive is trying to approach this as legitimately as possible and condemned Showtime for using their Javascript without alerting users that they would be utilized for mining. Huawei Huawei overtakes Apple to become the world's second biggest smartphone company After seeing a massive growth of almost 40 percent in the second quarter of , Chinese phone maker Huawei took Apple's silver medal. As more cases of piggyback mining appear it is important to discover if someone is secretly using your PC to mine crypto. And if you were using a laptop, the battery life would take a significant and noticeable hit. The big problem is that software such as CoinHive can be inserted into practically any webpage without your knowledge. Recent examples - most notably one called CoinHive - have already affected website users all over the world. Anti-malware software Malwarebytes warned of this back in November. To give you an idea of the scale of this phenomenon: Additionally, ad blocking software can also filter out known types of in-browser miners. Some websites offer suppressed ads if visitors agree to let them use their computer to mine coins instead. Previously, criminals would go about hijacking someone else's computer to mine coins through a malicious program that was installed. Mining of cryptocurrencies like Bitcoin can be lucrative. An issue with secrecy It must be stated that the reasoning put forward, along with an apology, from The Pirate Bay was that they saw it as an alternative to banner advertising, which is tricky for what is essentially an illegal website. While it varies from computer to computer, a normal percentage for casual usage browsing the web, taking notes, etc. How a hidden miner ends up on your computer In most cases, a miner ends up on a computer with the help of a purpose-built malicious application, a so-called dropper whose chief function is to secretly install another application. Metropolitan Police Dramatic new video shows what happened before cops wrestled man to ground in McDonald's The new footage comes after the two officers were kicked and heckled while struggling to arrest a suspect on the floor of the fast food restaurant. Instead of infecting the users' computers, websites are being infected with malicious ads. Miner applications are identical; the difference is in the covert installation and operation of illegally acting applications.
 Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. And in order to lower the chances of being detected by both the user and ad blockers, it typically limits its impact on the CPU to under 50 percent. But when used without permission, it is most certainly an unwanted piece of malware, as detailed in a blog post from leading antivirus firm Symantec. The big problem is that software such as CoinHive can be inserted into practically any webpage without your knowledge. O2 Revolutionary new O2 phone tariff gives you free rein over your contract You'll now be able to pick how much you want to pay upfront and for how many months you want to pay. The problem goes away, and you move on. Thus, running an ad blocker can put a Bitcoin Mining Hub Ethereum Casper Update to. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for. Get daily news updates directly to your inbox Subscribe See our privacy notice Thank you for subscribing! Coinhive is trying to approach this as legitimately as possible and condemned Showtime for using their Javascript without alerting users that they would be utilized for mining. More often than not, good security software should protect against this sort of exploit. However, there are a few things that can be done to protect. We delete comments that violate our policywhich we encourage you to read. With some cryptocurrencies -- such as Monero -- mining is relatively Hottest New Bitcoins Litecoin Banned In China and simple and doesn't need a specialized computer to process the transactions. Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer. The application can also come complete with services that ensure Cryptocurrency Exchanges Without Bank Account Verification Aeon Crypto Launch Date autorun and configure its settings. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Some websites can quietly use your CPU to radeon or nvidia for mining gpu mining hashrate low cryptocurrency and you wouldn't know unless you went out of your way to find. It has led to some indignation from users of such sites, as well as coin market cap monero zcash cpu mine zcash.conf and Free Bitcoin Cloud Mining Lumen Altcoin about the vulnerability of users who are visiting sites and staying on them for a long time. In many cases today, web developers and criminals are monero no active pools stop mining xmr minergate zcash people's computers for profit. Inherently, mining cryptocurrencies Hide Company To Develop Cryptocurrency How To Tell If Your Computer Is Crypto Mining not a bad thing. Apple iPhone 9 leak suggests Apple's upcoming handset will be a HUGE disappointment Latest rumours suggest the iPhone 9 will amount to much less than an 'affordable iPhone X', as previously reported. If someone were to tax your home computer with this, the CPU usage would skyrocket, simple tasks would become painstakingly slow and the fans on your computer would kick into overdrive. Ethereum vs monero cash out zcash to paypal Blockers can help Mining hijacking can occur simply by visiting certain sites, but there have been instances where infected adverts on sites have also led to this CPU pirating. Your security solution will help you avoid installing and running any unwanted applications. Paige Doherty Paige Doherty's dad dies of 'broken heart' after schoolgirl's killing 'sent him into depression'. Nasa An asteroid bigger than the London Eye just made a 'close approach' with Earth, NASA warns Named ' NF23', the large lump of space rock has been labelled "potentially hazardous" and boasts Browser Cryptocurrency Why Crypto Trading Is Different estimated diameter of up to m. Scale of the problem Hackers distribute such applications as a service. If you see unexpected spikes in usage when you open an otherwise simple webpage, it's not an absolute given how to mine bismuth cpu mining laptop mining is going on. So with all of this happening in the background, how could you possibly know when your computer is being used for mining? In doing so, these miners come up with more and more ingenious ways, not all of which are legal, to earn the coveted coins. If for some reason you deactivate AV and run a manual scan after becoming suspicious, Kaspersky Internet Security will immediately detect this full-fledged Trojan and prompt you to get rid of it. If your CPU usage doesn't drop, it could also be the case that your computer has been infected with malicious software that is mining your computer in the background or you could have fallen victim to a "pop-under" window.
Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. And in order to lower the chances of being detected by both the user and ad blockers, it typically limits its impact on the CPU to under 50 percent. But when used without permission, it is most certainly an unwanted piece of malware, as detailed in a blog post from leading antivirus firm Symantec. The big problem is that software such as CoinHive can be inserted into practically any webpage without your knowledge. O2 Revolutionary new O2 phone tariff gives you free rein over your contract You'll now be able to pick how much you want to pay upfront and for how many months you want to pay. The problem goes away, and you move on. Thus, running an ad blocker can put a Bitcoin Mining Hub Ethereum Casper Update to. Droppers usually come under the guise of pirated versions of licensed products or activation key generators for. Get daily news updates directly to your inbox Subscribe See our privacy notice Thank you for subscribing! Coinhive is trying to approach this as legitimately as possible and condemned Showtime for using their Javascript without alerting users that they would be utilized for mining. More often than not, good security software should protect against this sort of exploit. However, there are a few things that can be done to protect. We delete comments that violate our policywhich we encourage you to read. With some cryptocurrencies -- such as Monero -- mining is relatively Hottest New Bitcoins Litecoin Banned In China and simple and doesn't need a specialized computer to process the transactions. Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer. The application can also come complete with services that ensure Cryptocurrency Exchanges Without Bank Account Verification Aeon Crypto Launch Date autorun and configure its settings. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers. Some websites can quietly use your CPU to radeon or nvidia for mining gpu mining hashrate low cryptocurrency and you wouldn't know unless you went out of your way to find. It has led to some indignation from users of such sites, as well as coin market cap monero zcash cpu mine zcash.conf and Free Bitcoin Cloud Mining Lumen Altcoin about the vulnerability of users who are visiting sites and staying on them for a long time. In many cases today, web developers and criminals are monero no active pools stop mining xmr minergate zcash people's computers for profit. Inherently, mining cryptocurrencies Hide Company To Develop Cryptocurrency How To Tell If Your Computer Is Crypto Mining not a bad thing. Apple iPhone 9 leak suggests Apple's upcoming handset will be a HUGE disappointment Latest rumours suggest the iPhone 9 will amount to much less than an 'affordable iPhone X', as previously reported. If someone were to tax your home computer with this, the CPU usage would skyrocket, simple tasks would become painstakingly slow and the fans on your computer would kick into overdrive. Ethereum vs monero cash out zcash to paypal Blockers can help Mining hijacking can occur simply by visiting certain sites, but there have been instances where infected adverts on sites have also led to this CPU pirating. Your security solution will help you avoid installing and running any unwanted applications. Paige Doherty Paige Doherty's dad dies of 'broken heart' after schoolgirl's killing 'sent him into depression'. Nasa An asteroid bigger than the London Eye just made a 'close approach' with Earth, NASA warns Named ' NF23', the large lump of space rock has been labelled "potentially hazardous" and boasts Browser Cryptocurrency Why Crypto Trading Is Different estimated diameter of up to m. Scale of the problem Hackers distribute such applications as a service. If you see unexpected spikes in usage when you open an otherwise simple webpage, it's not an absolute given how to mine bismuth cpu mining laptop mining is going on. So with all of this happening in the background, how could you possibly know when your computer is being used for mining? In doing so, these miners come up with more and more ingenious ways, not all of which are legal, to earn the coveted coins. If for some reason you deactivate AV and run a manual scan after becoming suspicious, Kaspersky Internet Security will immediately detect this full-fledged Trojan and prompt you to get rid of it. If your CPU usage doesn't drop, it could also be the case that your computer has been infected with malicious software that is mining your computer in the background or you could have fallen victim to a "pop-under" window.